AQtive Guard Changelog↑
This is the list of version numbers of AQtive Guard and their deployment dates in SaaS at analyzer.cryptosense.com. Each version number is shown with a list of changes brought by that version.
25.06.2 - 2025-06-26↑
Bug fixes↑
- API & Backend
- Added two timeout configuration variables:
-
RQ_JOB_TIMEOUTto customize the redis queue task timeout (default is 2 hours) -REPORT_TIMEOUTto customize the report generation timeout -TRACE_TIMEOUTto customize the trace pre-analysis timeout - Fixed a bug when the an analysis timeout happens exactly while the report gets analyzed, leading to a wrong state race condition.
25.06.1 - 2025-06-13↑
Upgrade information↑
- Python has been updated to version 3.9.23
25.06.0 - 2025-06-12↑
On-premise upgrade information↑
- This version includes an automated database migration that merges existing duplicate keys or certificates. Because the deduplication process modifies data and deletes duplicate rows from the database, on-premises customers are advised to back up their database before upgrading.
What’s new↑
- API & Backend
- Improved analysis performance and scalability, particularly when the database contains a large number of global keys and certificates.
Bug fixes↑
- API & Backend
- Fixed an issue in the global key matching process that caused duplicate keys to be inserted when two parallel analysis processes independently discovered the same key.
- Prevented the application from reporting an error if a trace analysis request timed out. This occurred when a request remained in the queue for an extended period before being processed by a worker node, often due to an overload of analysis requests.
25.05.2 - 2025-05-23↑
Bug fixes↑
- API & Backend
- Fixed an issue where the Datadog Tracing Agent could cause application crashes.
25.05.1 - 2025-05-19↑
Bug fixes↑
- UI
- Fixed an issue that prevented downloads in the “Sensors” page
25.04.1 - 2025-04-24↑
Bug fixes↑
- API & Backend
- Fixed potential CSRF requests from HTML web forms by filtering relevant query headers
25.03.2 - 2025-03-13↑
Bug fixes↑
- API & Backend
- Added server-side session management to invalidate cookies after user logout
- Dropped on-premise package support for Ubuntu 18.04
25.02.4 - 2025-02-26↑
Bug fixes↑
- API & Backend
- Fixed an intermittent report generation error encountered when the number of filesystem scans exceeds a cap
25.02.3 - 2025-02-13↑
Bug fixes↑
- API & Backend
- Improved speed for the organization keys information page.
25.02.1 - 2025-02-04↑
Bug fixes↑
- API & Backend
- Resolved an issue where background workers would crash in a loop during startup when provided with a
rediss://URL - Fixed a bug where connection to Redis would fail when using TLS (
rediss) - Enhanced Java application analysis to improve detection of weak passwords
- Resolved an issue where background workers would crash in a loop during startup when provided with a
25.01.1 - 2025-01-21↑
What’s new↑
- API & Backend
- Enhanced Java application analysis to improve detection of key stores that do not have a password set
Bug fixes↑
- UI & Integrations
- Fixed the SandboxAQ favicon in the UI to support browser dark mode
25.01.0 - 2025-01-09↑
What’s new↑
- UI & Integrations
- Added CrowdStrike integration
- Added CrowdStrike settings and test connection functionality
- Allowed CrowdStrike to be used for Scan orchestration
- Added Scans page for filesystem scan orchestration
- Introduced new page where user can start a manual scan through CrowdStrike
- Added a table of scans with information of the scan status, success and number of affected hosts
- Added a nested hosts table with details of each host scan
- Added CrowdStrike integration
24.12.3 - 2024-12-20↑
What’s new↑
- API & Backend
- Improved detection of Password-Based Encryption issues in Java application analysis
Bug fixes↑
- API & Backend
- Resolved issue with temporary file management in Java application analysis
24.12.2 - 2024-12-18↑
Bug fixes↑
- API & Backend
- Security hardening for unsecured Redis connections
24.11.2 - 2024-11-19↑
What’s new↑
-
UI
- Added link in call site table to documentation to explain call site statuses
Bug fixes↑
-
UI
- Fixed broken links to Exceptions documentation
- API & Backend
- Fixed an issue with IAM database credentials being invalid when passed between running containers; this was causing analysis jobs to fail under some IAM policies.
24.11.1 - 2024-11-13↑
What’s new↑
-
API & Backend
-
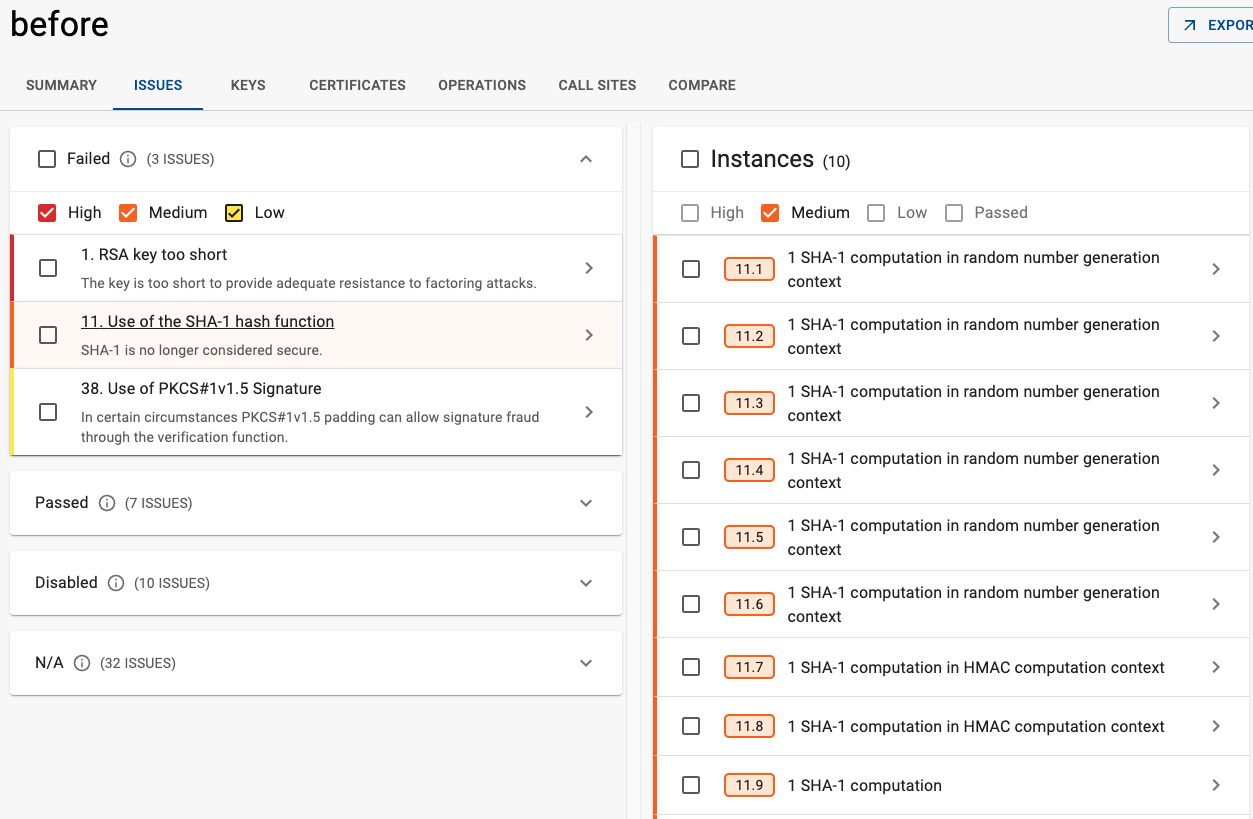
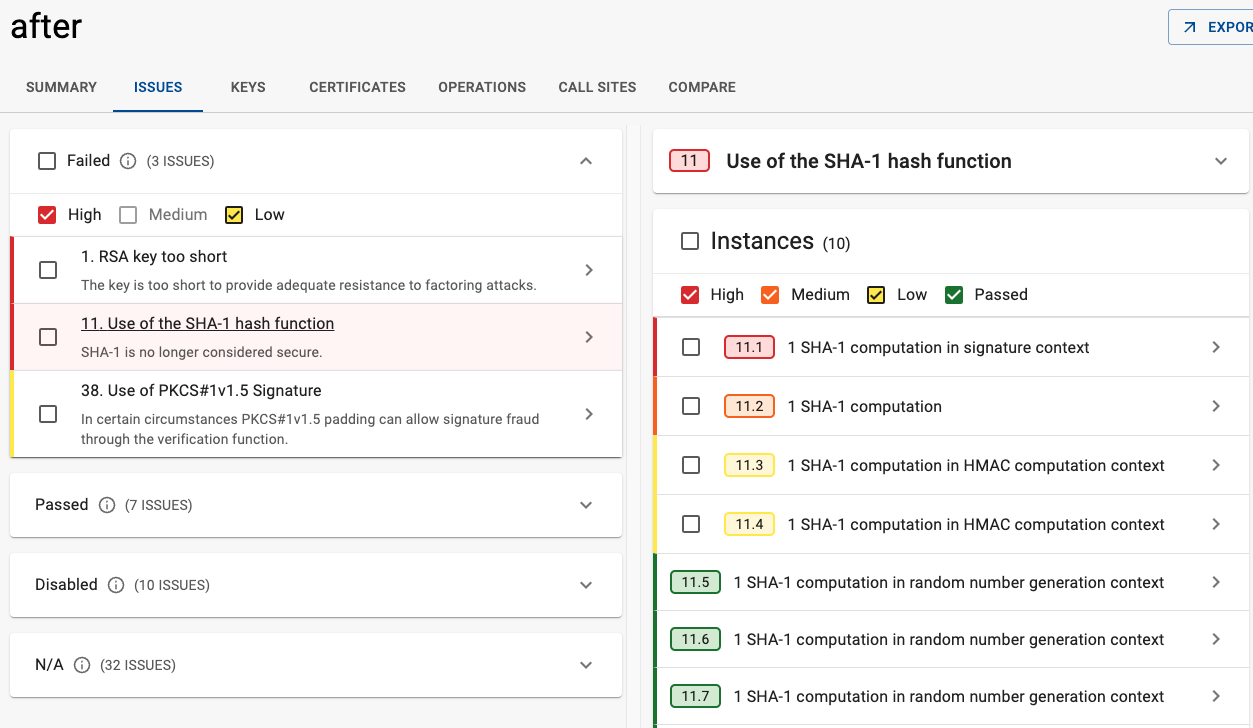
Modified the SHA-1 rule severity logic to consider context, providing a more precise risk assessment. Previously all uses of SHA-1 were rated as having Medium severity, the severity now depends on context as follows:
- If SHA-1 is used as part of random number generation: Pass
- If it is used for computing an HMAC: Low
- If it is used as part of a digital signature: High
- Any other use: Medium
Bug fixes↑
-
-
UI
- Fixed a UI bug with the display of “day” thresholds on profiles
- API & Backend
- Fixed an issue in Java application analysis where the call sites tab was showing large amounts of irrelevant data, both indirect call sites and call sites inside the Java cryptographic libraries
24.10.4 - 2024-10-30↑
What’s new↑
-
UI
- Enabled ServiceNow integration
- Allows creating ServiceNow incidents from one or more AQtive Guard instances through single export or bulk export
- Introduced ability to manually select issues/instances from a report to export to Jira or ServiceNow
- Exporting a report to Jira will export all failed instances instead of the 50 with highest priorities
- Exporting one or more instances to Jira or ServiceNow will persist the exported url for future reference
- Introduced the ability to cancel export to Jira or ServiceNow when exporting multiple instances
- Enabled ServiceNow integration
-
API & Backend
jiraExportInstancesnow returns fieldsexportType,status,totalCount,exportedCount,createdAt, andcanceledAt`- Exposed
cancelJiraExportto cancel a bulk export to Jira - Exposed
updateServiceNowIntegrationto configure ServiceNow integration - Exposed
checkServiceNowIntegrationto validate ServiceNow configuration - Exposed
unlinkServiceNowIntegrationto unlink a ServiceNow integration - Exposed
serviceNowExportInstanceto export a single instance to ServiceNow - Exposed
serviceNowExportReportto export an entire report to ServiceNow - Exposed
serviceNowCancelReportExportto cancel a bulk export to ServiceNow
Bug fixes↑
- API & Backend
- Fixed an issue preventing the analysis of SSH handshakes with DH group exchange
24.10.3 - 2024-10-23↑
What’s new↑
- API & Backend
- Updated the
jira_export_instancemutation:- Revert deprecation in favor of allowing a controlled single instance export
- Updated validations to match the latest changes around JIRA connections
- Updated the
Bug fixes↑
- API & Backend
- Deleting the last report of a profile will immediately delete the profile, instead of after a delay
- Updated JIRA Connection Checker to explicitly check for the existence of an issue type
24.10.2 - 2024-10-16↑
What’s new↑
-
UI
- Updated project creation and flow validation
- Don’t apply upper limit when organization has licensed unlimited reports.
- Updated project creation and flow validation
- API & Backend
- [GraphQL]:
- Added the
ReportDone.locationsconnection to retrieve all locations found in a report - Added filtering support to the
Location.instancesconnection
- Added the
- [GraphQL]:
24.10.1 - 2024-10-09↑
What’s new↑
- API & Backend
- Added the inputs
fromDateandtoDatetoOrganization.overviewto allow getting overview summary based on date range
- Added the inputs
Bug fixes↑
- UI
- Fixed a UI bug where some threshold rule values were not displayed when viewing profiles in read-only mode
- Fixed a bug where the export of the dashboard into overview.csv does not take into account selected time period
24.10.0 - 2024-10-02↑
What’s new↑
-
UI
- Improved display of time ranges in the Organization Dashboard Instance Summary charts
- API & Backend
- Enabled Tanium integration for retrieval process with features like:
- Migrated the project settings to a new UI
- Enhanced retrieval logs with more detailed and enriched data for every retrieval step
- Allow log download while the retrieval is in progress
- Introduced additional configuration options for reattempts of retrieval steps
- Enabled Tanium integration for retrieval process with features like:
Bug fixes↑
-
UI
- Fixed a regression that would prevent users from exporting a single instance to Jira
- Corrected a typo in documentation that would prevent uploading traces in java tracer streaming mode.
- API & Backend
- Fixed an issue where some “low” and “medium” threshold values were incorrectly flagged as “high” severity
- Tanium bug fixes
- Tanium Retrieval is now done through concurrent worker job. This releases locked worker resources so that other queued jobs can also take place.
- Log is no more limited to 30.000 characters
- When updating computer group in settings, it is double-checked that the group actually exists on Tanium instance
- During retrieval, there is a check to see if there is a trace file on the endpoint
- General error handling for unexpected cases for each retrieval step is introduced
24.09.2 - 2024-09-11↑
What’s new↑
- API & Backend
- Released Java Tracer version 2.2.1. Check Java tracer changelog for more information
- Added support for streaming flow over the API. As part of that, included multiple new mutations to support the said flow
- Added
createStreamUploadmutation that creates new stream upload and provides stream id for additional stream actions - Added
generatePresignedPartUrlsmutation that provides a list of presigned urls for upload of several stream parts - Added
finalizeStreamUploadmutation that runs the finalization process for the upload and starts an analysis over the stream - Added
refreshStreamUploadmutation that heart-beat for stream upload, updates tracker of stream activity
- Added
24.08.4 - 2024-08-28↑
What’s new↑
- UI
- New Settings dropdown in the menu bar consolidates system configuration and API options:
- Users - Create, edit, or manage AQtive Guard user accounts.
- Integrations - Configure an integration between AQtive Guard and supported external systems.
- Profiles - Create and manage Profiles, which define the criteria for cryptographic analysis.
- Sensors - Explore the available AQtive Guard sensors.
- API - Use the API Explorer to send requests and view responses for interacting with the AQtive Guard API.
- Migrated Knowledge Base (cryptographic information and best practices) to a central repository
- Added footer with a link to the official Accessibility Statement
- New Settings dropdown in the menu bar consolidates system configuration and API options:
24.08.3 - 2024-08-21↑
What’s new↑
- API & Backend
- Improvement: Rule 75 that detects quantum vulnerable ciphersuites in Network reports is disabled for now since it has been replaced by rules 66 and 68 that look separately into signature and kex algorithms.
- [GraphQL]: Added the
ReportsFilter.traceTypeandTracesFilter.traceTypefields to filter reports and traces based on their trace type. These filters can be applied on theProject.traces,Slot.traces,Project.reports,Slot.reportsandTrace.reportsconnections.
Bug fixes↑
- UI
- Change formatting of Digest algorithm on the Report and Organization Certificates pages for filter dropdown to be consistent with table content
24.08.2 - 2024-08-16↑
What’s new↑
- API & Backend
- Update Network Analyzer configuration to allow sensor download.
Bug fixes↑
- API & Backend
- Fixed the error when creating a new project in some configurations
24.08.1 - 2024-08-14↑
What’s new↑
-
UI
- Add Network Analyzer to sensors page.
- API & Backend
- Support IAM authentication type when configuring managed secrets with the
DATABASE_URLlabel. Example Usage:DATABASE_URL='postgresql://:@<rds-ip-or-hostname>:5432/postgres'SECRET_PROVIDER='{"provider": "aws", "config": {"region_name": "<region>"}, "labels":{"DATABASE_URL": {"label": {"hostname": "<rds-hostname>", "username": "postgres", "port": 5432}, "encoding": "RAW", "auth_type": "IAM"}}}'- For more details, refer to the configuration documentation.
- Support IAM authentication type when configuring managed secrets with the
Bug fixes↑
- UI
- Fixed the case when an instance is exported to Jira, the Jira url persists on non-exported instance views
24.08.0 - 2024-08-07↑
What’s new↑
- UI
- Added the “Sensors” page to view AQtive Guard sensors available for download, along with their version and documentation links
Bug fixes↑
-
UI
- Improved error handling and feedback of the Jira Issue Export configuration flow
- Fixed an issue that could cause navigation breadcrumbs to show outdated values after projects or slots are renamed
- Fixed an issue that could cause changing page in the Report Operations table to fail when sorted by the “Timestamp” column
-
API & Backend
- Fixed a regression introduced in release 24.05.5 that caused Key Stores identified in new reports to not be displayed in inventory charts. Key Stores were still correctly identified, and will now be displayed for all existing and new reports.
24.07.3 - 2024-07-31↑
What’s new↑
-
UI
- The menu bar is now displayed on the API Explorer and Knowledge Base pages
- The Jira issue collector now includes the rule number and local instance number when the summary is populated
- API & Backend
- An instance exported to Jira now includes the rule number and local instance number in the summary
Bug fixes↑
- UI
- Updating a profile with a name that already exists now shows a clearer error message
- Fixed an issue that would cause the Inventory “Operations” charts to be empty for organizations without network reports
- TLS and SSH handshakes operations are now displayed in the Inventory “Operations” charts
24.07.2 - 2024-07-24↑
What’s new↑
-
UI
- Inventory charts in the Organization Dashboard, Project Overview and Report Summary now account for Network reports
- “Priority fixes” in the Organization Dashboard and “Priority issues” in the Project Overview are now sorted by descending severity, descending number of reports impacted, and ascending rule number
- The reports of expanded issues in the Project Overview are now sorted by descending number of failed instances
- Design improvements for the expanded display of the “Projects” table and the “Issues” display of the “Project Overview”
- API & Backend
- [GraphQL]:
- Network reports are now included in the result of the
Organization.inventory,Project.inventoryandReportDone.inventoryfields - Edges of the
Organization.vulnerabilities,Project.vulnerabilitiesandReportDone.vulnerabilitiesare now sorted by descendingseverity, descendingnumberOfSlots, ascendingnumber - Edges of the
Vulnerability.slotsandReportVulnerability.slotsconnections are now sorted by descendinginstancesFailed
- Network reports are now included in the result of the
- Parse, analyze, store and display SSH handshakes from network captures.
- Parse, store and display Dilithium, Falcon and Sphincs keys.
- Independently analyze key exchange and signature algorithms for PQ readiness in TLS handshakes.
- [GraphQL]:
Bug fixes↑
- UI
- Minor ADA compliance fixes for charts and expandable content across pages
24.07.1 - 2024-07-17↑
What’s new↑
-
UI
- The “Users” table can now be sorted by its “Preferred name” and “Account type” columns
- Added the “Preferred name” filter to the “Users” table
- Added the “Account type” filter to the “Users” table
- Added the “Roles” filter to the “Users” table
- The Report “Inventory” tab has been renamed to “Summary” for all types of report
- API & Backend
- [GraphQL]:
- Added the
UsersSorterFields.preferredNamefield to sort users based on their preferred name - Added the
UsersSorterFields.originfield to sort users based on their account type - Added the
UsersFilterFields.preferredNamefield to filter users based on their preferred name - Added the
UsersFilterFields.originfield to filter users based on their account type - Added the
UsersFilterFields.rolesfield to filter users based on their permission roles
- Added the
- [GraphQL]:
24.07.0 - 2024-07-12↑
What’s new↑
-
UI
- Added support for SSH handshakes in network reports: use the “Protocol” selector in the Report “Handshakes” tab to view TLS or SSH handshakes identified in the uploaded trace
- The “Ciphersuites” table of network reports now supports pagination
- The “Profiles” table now shows predefined profiles first, followed by custom profiles from most to least recently created
- The “Users” table now shows the current user first, followed by other users from most to least recently created
- The “Reports” table of a Project is now sorted by most to least recently created slot
- Changed the default page size of all tables to 10 rows to reduce scrolling and improve accessibility
- Added shortcuts to go to the first and last page of tables
- The “Projects”, “Profiles” and “Tags” filters in the Organization Dashboard now always display the current selection before additional available items
- Added the “All time” shortcut to the Organization Dashboard time range filter
- The Report Inventory “Crypto Library Security” table is now included in Report Print exports
- The “Type” column of “inventory.csv” file in bundled Organization, Project and Report CSV export ZIP files is now sorted similarly to the pie charts in the web UI
- The “cryptography_operations_statistics.csv” file in the bundled Report CSV export ZIP file has been renamed to “statistics.csv”
- API & Backend
- Support live rotation of managed secrets with the
DATABASE_URLlabel (e.g. via AWS Secrets Manager) - Default report name is changed from “Report 1 for {trace name}” to “Report for {trace name}”
- [GraphQL]:
- Added the
SlotsSorterFields.idsorter to sort slots based on their ID - Added the
UsersSorterFields.idsorter to sort users based on their ID - Added the
UsersSorterFields.currentsorter to sort users based on whether they are the current user - Added the
ProfilesSorterFields.presetsorter to sort profiles based on whether they are predefined AQtive Guard profiles
- Added the
- Support live rotation of managed secrets with the
Bug fixes↑
- UI
- Fixed an issue in the Report “Ciphersuites” table that could cause clicking on a row to not apply the corresponding filter on the Handshakes table
24.06.4 - 2024-06-27↑
What’s new↑
- UI
- The Jira integration configuration will now validate the project key and issue type, and only allow updates with values that pass the check
- Exporting to Jira will validate that the issue type has the required issue fields and priority values prior to allowing export
24.06.3 - 2024-06-24↑
What’s new↑
-
UI
- The “Handshakes” table for Network Reports now only displays a single “Timestamp” that describes when the handshake took place
- The “Client timestamp” and “Server timestamp” filters have been replaced by the “Timestamp” filter
- The input of the “Timestamp” filter in the Report “Operations” and “Handshakes” tables now reflects the format of the table column
- API & Backend
- [GraphQL]:
- Exposed the
checkJiraIntegrationmutation to confirm project key and issue type exist on the Jira client - Exposed the
checkJiraExportmutation to confirm issue type has required issue fields and priority values before export - Renamed
client_timestampinHandshaketotimestamp. - Removed
server_timestampinHandshake.
- Exposed the
- Added
RC5analysis and enhanced2-key-3DESreporting. - Support retrieving RDS credentials in AWS-based deployments by using the
"JSON"encoding option in theSECRET_PROVIDERenvironment variable.- Refer to the On-premise installation Configuration reference for more information.
- [GraphQL]:
Bug fixes↑
-
UI
- Improved ADA compliance of the “Integrations” page
- Improved reachability and keyboard navigation of the Organization Dashboard “Instance summary” bar chart
- The “Timestamp” filter in the Report “Operations” and “Handshakes” tables now uses the UTC timezone instead of the browser’s local timezone
- API & Backend
- Fixed an error that would prevent slots and projects from being deleted if they contained report diffs
- Fixed a bug where the analyzer sometimes attempted to insert the same certificate into the database twice, causing a unique constraint violation
- [GraphQL]:
- The
HandshakesFilterFields.initiator_portandHandshakesFilterFields.target_portfilters now fail gracefully if the input is not a port number - The
HandshakesFilterFields.timestampfilter now fails gracefully if the input is not a ISO-8601 datetime string
- The
24.06.2 - 2024-06-12↑
What’s new↑
-
UI
- Added the “Algorithms” filter to the Report Operations table
- Improved Table Filtering with enhanced accessibility and user experience:
- Replaced the magnifying glass icon with a Search target above the first column
- Filters are always available for easier access
- API & Backend
- [GraphQL]:
- Added the
OperationAlgorithmenum that lists all algorithms that can be used by any type of operation - Added the
OperationsFilterFields.algorithmsfilter to allOperationConnections - The filter can be used with the
CONTAINSoperator to retrieve operations based on their algorithm usage valuesmust be a list ofOperationAlgorithm: if more than one algorithm is provided, only operations that used all of them will be returned
- Added the
- [GraphQL]:
Bug fixes↑
- API & Backend
- Fix an error that would prevent slots and projects from being deleted if they contained report diffs
24.06.1 - 2024-06-05↑
What’s new↑
-
General/Notes
- Upgrading to this release might take longer due to database modifications
-
UI
- The Report “Call sites” page has been migrated to the new design language of AQtive Guard
- The “API” pages have been consolidated into a single page which gathers the “API Explorer”, “Reset key” and the link to the “API Documentation”
- Added the Report “Operations” tab to display all cryptographic operations identified in the analysis of compatible traces
- The “Operation Details” page has been migrated to the new design language of AQtive Guard, and displays additional information about instances, calls, keys and handshakes linked to a cryptographic operation
- Projects Table
- The “Last updated” column of the Projects table has been renamed to “Last analysis”
- The Projects table can now be sorted by its “Last analysis” column
- The browser’s title bar now displays information about the current page instead of a generic “AQtive Guard”
- API & Backend
- [Configuration]:
- Added the optional configuration parameter
SESSION_DURATION_SECONDSto set the timeout of web sessions. Default value is set to 86400 (24 hours)
- Added the optional configuration parameter
- [GraphQL]:
- Added the
ProjectsSorterFields.lastAnalysisfield to sort projects based on their last created or completed report - Added the
ProjectsFilterFields.lastAnalysisfield to filter projects based on their last created or completed report - The
Project.lastUpdatedfield has been deprecated and will be removed in a future release. Use theProject.lastAnalysisfield instead - The
ProjectsFilterFields.lastUpdatedfilter has been deprecated and will be removed in a future release. Use theProjectsFilterFields.lastAnalysisfilter instead
- Added the
- [Configuration]:
Bug fixes↑
- UI
- Fixed an issue that could cause a blank page to be rendered when using Print exports in Firefox
- Fixed an issue that would cause Print exports to display truncated, small or misaligned elements in Firefox and Safari
24.05.5 - 2024-05-30↑
What’s new↑
-
UI
- Improved keyboard navigation and screen reader experience of table filters
- The “Key store” and “Hash functions” links in the Organization and Project inventory now open in a new tab
- API & Backend
- [GraphQL]:
- Added the
ENABLE_GRAPHQL_INTROSPECTIONconfiguration value to enable API introspection queries (default: false). When introspection is disabled, the API Explorer will not provide suggestions or details about the schema - The
updateTaniumIntegrationmutation now accepts therequestTimeoutanddownloadRequestTimeoutinputs to configure timeouts. Acceptable values must be in the range specified by the configuration values above - Added the
requestTimeoutanddownloadRequestTimeoutfields to theTaniumIntegrationtype
- Added the
- [Tanium]: added the following configuration values:
TANIUM_REQUEST_TIMEOUT: used for all Tanium requests, except download (default: 30 seconds)TANIUM_MIN_REQUEST_TIMEOUT: minimum allowed configurable request timeout value (default: 30 seconds)TANIUM_MAX_REQUEST_TIMEOUT: maximum allowed configurable request timeout value (default: 300 seconds)TANIUM_DOWNLOAD_REQUEST_TIMEOUT: specific request timeout value for the download operation (default: 90 seconds)
- [GraphQL]:
Bug fixes↑
-
UI
- The AQtive Guard logo is now correctly displayed in browser tabs and pinned bookmarks for all pages
- Fixed an issue that allowed entering invalid inputs in the Report Handshakes source and destination port filters
- Fixed an issue that allowed filtering Report and Organization Keys with invalid configurations
- Fixed an issue that could prevent table filters from updating on field change
- The Inventory pie charts in the Organization and Project dashboard are now reachable via keyboard navigation
- The Instance Summary pie chart in the Organization Dashboard is now reachable via keyboard navigation
- API & Backend
- Fixed an issue that caused OIDC login to fail if the
OIDC_USER_DISPLAY_NAMEoption is not configured - [GraphQL]:
- The
Project.taniumfield now returnsnullifProjectTanium.computerGroupis unset - The
Organization.usersandOrganization.testersconnections will now return an empty list if the current user does not have permission to view other Users
- The
- Fixed an issue that caused OIDC login to fail if the
24.05.4 - 2024-05-22↑
What’s new↑
-
UI
- Adding a link to download the log file
- API & Backend
- [GraphQL]:
- Added the
OperationTypeenum - Changed the return value of
Operation.typefrom string to a value of theOperationTypeenum- Use the
Operation.operationTypefield to retrieve the string value
- Use the
- Added the
- Added the following fields to
OperationsFilterFieldsandOperationsSorterFieldstype: value of theOperationTypeenumcategory: value of theOperationCategoryenum
- [GraphQL]:
24.05.3 - 2024-05-09↑
What’s new↑
- General/Notes
- Reverted user documentation login requirement from 24.05.2
24.05.2 - 2024-05-08↑
What’s new↑
-
General/Notes
- Note: This release might take longer time to upgrade because of database modifications
- Login will be required to access user documentation.
-
UI
- Help texts/Tooltips are now available on the organization dashboard and report inventory.
- Disabled fields/buttons if the user does not have permission to edit Tanium. Added an alert message to explain why the fields are disabled
-
API & Backend
- Stackframe IDs have been migrated from integer to biginteger type in PostgreSQL
- [GraphQL]:
- Added the type and category fields to operation filters and sorters
Bug fixes↑
- UI
- Fixed toggle on trends dropdown click
- Added titles to the tanium svgs for accessibility
24.05.1 - 2024-05-01↑
What’s new↑
-
UI
- Handshakes and calls timestamps are now formatted as a ISO-8601 string
-
API & Backend
- [GraphQL]:
- Added
CallSites.statusfield sorter toCallSitesSorterto sortReport.callsites - Added
CallSitesSorterandCallSitesFilterto sort and filter theReport.callsitesconnection based onCallSitesfields Report.operations,Key.operations,Instance.operationsandCertificate.operationsconnections can now be sorted and filtered- available
sorters:id,context,timestamp - available
filters:context(aOperationContextvalue),timestamp(a ISO-8601 datetime string)
- available
- Added the
Operation.contextfield that returns aOperationContextenum value - Added the
Operation.firstCallSitefield - Added the following fields to the
edgeof theOperation.keysconnectionrole: the role of the key in the operationcipherData: for encryption or decryption operations, the encrypted or decrypted datawrappedKeyId,wrappedByKeyId: for wrapping or unwrapping operations, the ID of the keys involved
- Added the
Report.operationsconnection to retrieve all operations found in a report - Added the
Operation.instancesconnection to retrieve all instances linked to an operation
- Added
Bug fixes↑
- [GraphQL]:
- UI
- Improved accessibility compliance, keyboard navigation and screen reader experience of the Organization Dashboard filters
- The Organization Dashboard “Profiles” filter now displays the profile type
24.04.2 - 2024-04-24↑
What’s new↑
-
UI
- Added report certificate sorters
- Added project slots sorters
- Sorting implemented for Report -> Certificates based on
- id
- expiry date
- digest algorithm
- fingerprint
- API & Backend
- [GraphQL]:
- Added
CertificatesSorterto sort and filter theReport.certificatesconnection based onCertificatefields
- Added
- Added TLS vulnerable ciphersuites rules for network analysis for DES, 3DES & RC4
- [GraphQL]:
Bug fixes↑
- UI
- Fixed the invisible close button on GraphQL dialogs
24.04.1 - 2024-04-17↑
What’s new↑
- API & Backend
- [GraphQL]:
- Added the
Operation.timestampfield - Added the
Operation.valueJsonfield - Added the
Operation.callsconnection - The
Instance.operations,Instance.callsandOperation.callsconnection can now be filtered using thekept_by_filtersargument:true: return only operations and calls that are kept by project exceptionsfalse: return only operations and calls that are removed by project exceptionsnullor unset: return all operations and calls
- Added the
- Added new
cs logs bundletool for on-premises deployments to inspect, filter and merge logs emitted byAQtive Guardservices. You can consult thecs logs bundle --helpfor all the options offered.
- [GraphQL]:
24.04.0 - 2024-04-10↑
What’s new↑
-
UI
- Pages migrated to the new UI:
- Dashboard trends
- Project settings & exceptions configuration
- Report comparison & summary
- Profiles listing & definition
- Pages migrated to the new UI:
- API & Backend
- Improve rules to detect TLS ciphersuites that use DES/3DES/RC4
- Add a
logssub-command to thecson-premises command to inspect, merge and filter logs - Expand the Tanium-related GraphQL API for a project:
- Ability to get the associated computer group and status-related field of a running scan
- Mutation to stop a Tanium scan
Bug fixes↑
-
UI
- Add visibility to missing rules for the filesystem scanner (formerly host scanner) on the profile page
- Fix breadcrumbs display on some legacy pages
- API & Backend
- Disable manual Python garbage collection in the default configuration
- Make the host-scanner resistant to zip bombs (#4709)
24.03.5 - 2024-04-04↑
What’s new↑
- UI
- Once the user has configured Jira, the base url will be displayed in a non-editable field.
- API & Backend
- Logs emitted by
analyzer/workerworkers during report generation will now containrequest_id, which is equal to theidof the HTTP request that uploaded the trace, thereby initiating the report generation. - Added the possibility to exclude common root certificates from the analysis. The default common root certificates list is based on Mozilla Included CA Certificate List. Certificates excluded by this feature are still parsed and stay in the inventory but no issue is created from their content. This feature is turned on by default for preset profiles but not for older custom profiles. Activating it or not when creating a new custom profile is a choice.
- Logs emitted by
Bug fixes↑
-
UI
- Accessibility (a11y) improvements & fixes for profile view & create
- API & Backend
- Fixed an issue with analyzer crashing when trying to handle a certificate with start date in the year 0.
- JKS keystores containing a malicious negative count of certificates or keys are not producing exceptions anymore and raising a clean parse_size failed: negative size warning instead.
- JCEKS keystores containing a maicious negative count of certificates or keys are not producing exceptions anymore and raising a clean parse_size failed: negative size warning instead.
- JCEKS containing a Secret Key entry containing a maliciously formatted utf8 or longutf8 are not are not producing exceptions anymore and raising a clean parse_size failed: negative size warning instead.
24.03.4 - 2024-03-27↑
What’s new↑
-
General
- Sandbox Security Suite is now AQtive Guard
-
UI
- Introduced organization dashboard Trends behind a feature flag.
- Reorganized filters with respect to Trends.
- API & Backend
- Logs contain new
request_idfield.request_idis a unique value for each request and enables correlation of logs originating across different sources - [GraphQL API]:
- Added the filter
overviewTypestoOrganization.inventoryfield - Added the filter
from(date) toOrganization.inventoryfield - Added the filter
to(date) toOrganization.inventoryfield - Added the filter
overviewTypestoOrganization.overviewfield - Added the filter
overviewTypestoOrganization.vulnerabilitiesfield - Added the filter
from(date) toOrganization.vulnerabilitiesfield - Added the filter
to(date) toOrganization.vulnerabilitiesfield - Added the filter
withExceptionstoOrganization.vulnerabilitiesfield - Added the filter
overviewTypestoOrganization.timeRepresentationSlicesfield
- Added the filter
- Logs contain new
Bug fixes↑
- UI
- Accessibility (a11y) improvements & fixes
24.03.3 - 2024-03-21↑
What’s new↑
-
UI
- Added viewing, creating and duplicating fuzzer profiles
- API & Backend
- [GraphQL API]:
- Added the
Profile.projectCountfield - Added incomplete TLS handshakes in the handshake listing of a report in the UI
- Removed TlsOrphanHandshake type and ‘orphanHandshakes’ connection in GraphQL
- Added TlsHandshakeStatus enum and TlsHandshake.status field in GraphQL
- Added new ‘statuses’ argument to ‘handshakes’ connection in GraphQL
- Added the
- [GraphQL API]:
Bug fixes↑
-
UI
- Print button is disabled for empty project
- API & Backend
- Fixed an issue that allowed profiles used as default profiles in projects to be deleted
- [GraphQL API]:
- The
deleteProfilepermission is not granted if the profile has been used by reports or projects
- The
24.03.2 - 2024-03-13↑
What’s new↑
-
General
- With key product updates under way, please expect changes to product URLs.
- API & Backend
- For on-premise deployments, postgres version has been updated to 12.18
Bug fixes↑
- UI
- Fixed an issue with api/v2/auth to return HTTP 401 Unauthorized response for invalid credentials, rather than HTTP 400 Bad Request if invalid user credentials are used.
24.03.1 - 2024-03-06↑
What’s new↑
- API & Backend
- [GraphQL API]:
- Added the
Project.exceptionsconnection to retrieve the exceptions of a project - Added
ProjectExceptionsSorterandProjectExceptionsFilterto sort and filter theProject.exceptionsconnection based onProjectExceptionfields - Added the
updateProjectExceptionmutation to update an existing project exception - Added the
deleteProjectExceptionmutation to delete a project exception
- Added the
- Expose
Profilemodel with multiple new fields- Added
createTracerProfilemutation - Added
createFuzzerProfilemutation - Added
updateTracerProfilemutation - Added
updateFuzzerProfilemutation - Added
deleteProfilemutation
- Added
- [GraphQL API]:
Bug fixes↑
-
UI
- A11y fixes on project settings tab
- API & Backend
- [GraphQL API]:
- Fixed an issue that caused
Callretrieval by id to fail
- Fixed an issue that caused
- [GraphQL API]:
24.02.4 - 2024-02-28↑
What’s new↑
- API & Backend
- Support
raw,unicode, andurl-encodedsecrets in AWS SECRETS Manager through updatedSECRETS_PROVIDERconfiguration option. If optionalencodingparam is unspecified, secrets are assumed to berawstrings by default - [GraphQL API]: Added the following fields to
PermissionsupdateUserPreferredName: granted if the current user can change thepreferredNameof the target userupdateUserPermissions: granted if the current user can change thelevelorrolesof the target userupdateUserAuthTags: granted if the current user can change theauthTagsof the target user
- Support
Bug fixes↑
- API & Backend
- [GraphQL API]:
- Fixed an issue that caused invalid results on paginated connections when sorted by
idin descending order - All fields of
Permissionsare now required. In case permission is not granted, adeniedReasonis always provided - Fixed an issue that allowed users without access to a report to be able to view its query calls by
callId - Fixed an issue that caused unhandled errors on invalid filters and sorters inputs
- Improved resiliency of mutations against several error scenarios, and added clarity to error messages in such cases
- Strengthened access policy validation throughout queries and mutations
- Fixed an issue that caused invalid results on paginated connections when sorted by
- [GraphQL API]:
24.02.3 - 2024-02-21↑
What’s new↑
-
Breaking Changes
- [GraphQL API]:
- The fields Organization.keys and Organization.certificates now return an empty connection for users with the “tester” level
- This is part of a security fix to prevent unauthorized access to data by testers
- [GraphQL API]:
- API & Backend
- [GraphQL]:
- Exposed
lastUsedandtimesUsedvalues on Profile model - Removed the
createOpenIdUsermutation. OpenID users should be created in the OpenID provider and configured with the appropriate claims - Updated the
createLocalUsermutationname: must be unique in the organization. Leading and trailing whitespaces are ignored and is case insensitivepreferredName: optional display name for the user. Leading and trailing whitespaces are ignoredlevelandroles: based on the authorization model and permissionspassword: must be at least 8 characters long. Leading and trailing whitespaces are ignoredauthTags: if available in the system
- Updated the
updateUsermutationpreferredName: optional display name for the user. Leading and trailing whitespaces are ignoredlevelandroles: based on the authorization model and permissions. This argument should not be used to update OpenID users with authorization managed via theOIDC_ROLE_CLAIM_NAMEandOIDC_ROLE_GROUP_MAPclaimsauthTags: if available in the system
- Exposed
- [GraphQL]:
Bug fixes↑
- API & Backend
- For OpenID Connect, the
preferred_usernametoken claim is now evaluated at each login to update thepreferredNameof OpenID users
- For OpenID Connect, the
24.02.2 - 2024-02-14↑
What’s new↑
-
UI
- By default, projects in the Projects table are now arranged in decreasing order by their creation date (most to least recent)
- API & Backend
- Added
OIDC_SERVER_CERTconfiguration option, which allows customers to set their own CA bundle for OpenID Server SSL Verification. IfOIDC_SERVER_CERTis unset or invalid, requests to OpenId Servers will default to the CA bundle used by underlying OS for SSL verification, rather than the CA bundle used by therequestslibrary
- Added
Bug fixes↑
-
UI
- Accessibility fixes on the users page
- API & Backend
- Error handling fixes in jira mutations
- Fixed flaky behavior with upload and analysis of small traces which sometimes resulted in failed uploads, failed analysis or empty reports
24.02.1 - 2024-02-08↑
What’s new↑
- UI
- Integrations page migrated to the new UI
Bug fixes↑
- UI
- Fixed failure with CSV export
- Fixed an issue with pie chart and other components shifting when the length of the instance count changes
- Accessibility fixes in the Reports table
24.02.0 - 2024-02-01↑
What’s new↑
- API & Backend
- opt-out flags are available to opt out of gql and stacktrace logging
- [GraphQL]:
- Exposed checkVenafiIntegration mutation
- Exposed checkTaniumIntegration mutation
- Exposed updateVenafiIntegration mutation
- Exposed updateTaniumIntegration mutation
- Errors executing GraphQL queries will now log a (sanitized) version of the query.
- Added a
jiraExportInstancesmutation to create multiple JIRA issues in bulk- the input must be a non-empty list of at most 50 instance IDs
- for each instance, the mutation returns either a
JiraExportIssueobject with the details of the JIRA issue, or aJiraExportErrorobject with additional details about the reason of the failure - The
jiraExportInstancemutation has been deprecated and will be removed in a future release. Users are invited to use thejiraExportInstancesmutation instead.
- Log entries with exception info are included in the stacktrace
- For on-premise installations, the configuration file update timestamp will no longer change if the configuration didn’t change
- [Optimization]: Requesting
Instance -> callsGraphQL connection is now faster
Bug fixes↑
-
UI
- A clear error message is shown to users for oauth error when clicking Link if the config is not done properly
- Fix to reset the URL to remove the filter query params when filters are cleared
- Accessibility fixes & improvements in organization/project and project/slots
- API & Backend
- All ssh keys in a file are parsed and analyzed, instead of the first one
- Fixed an issue that could cause calls to be displayed as filtered by the project exceptions in projects without exceptions
24.01.2 - 2024-01-24↑
What’s new↑
- API & Backend
- Added client IP address to audit logs:
client_ipkey records the IP address of the client sending the event request,the value is null if the detail is not available.forwarded_for_client_ipkey records the original client IP address in case of proxy connection. It is set to theX-Forwarded-Forheader in the event request, or null if not available.
- Added client IP address to audit logs:
Bug fixes↑
- UI
- Accessibility fixes in project/dashboard, project/slots
24.01.1 - 2024-01-18↑
What’s new↑
-
General
- AQtive Guard documentation is now shipped & available with the software itself at http://hostname/docs
-
UI
- The call_count column has been removed from the CSV export at the report level
- API & Backend
- [Optimization]:
- Querying
locationsofKeysandCertificatesis now faster - Querying
keysandcertificatesofLocationsis now faster
- Querying
- [GraphQL]: Added the
severitiesfilter toOrganization.vulnerabilities - The host-scanner can detect .sst files (“Serialized Certificate Store files” used by Windows machines to store certificates).
- [Optimization]:
Bug fixes↑
-
UI
- Updated UI text to clarify export limitations
- API & Backend
- Information about a ‘key’ for HostScanner reports are sorted descendingly in order of number of occurences
24.01.0 - 2024-01-11↑
What’s new↑
-
UI
- In Handshakes filter, only selected ciphersuites will be shown
- API & Backend
- [Optimization]: Requesting
ciphersuitestied to aReportDoneis now faster
- [Optimization]: Requesting
Bug fixes↑
-
UI
- Fixed an issue that prevented the Project Reports table to reflect changes to a slot after editing
- The type of a Profile (tracer or fuzzer) is now consistently displayed in the UI
- API & Backend
- Fixed an issue that prevented Venafi error messages to be correctly displayed
- Fixed an issue with the Report CSV export that could result in download failure or incomplete content
- GraphQL: Added Jira configuration on Project level
23.12.1 - 2023-12-14↑
What’s new↑
- API & Backend
- [GraphQL]:
Report.instancesandRule.instancescan now be sorted and filtered byInstance.numberLocal
- JIRA bulk exports are now limited to 50 instances at a time
- [GraphQL]:
Bug fixes↑
- API & Backend
- Fix trace uploads through the UI when STORAGE_USE_PUT is set to
true - Error logs generated by misconfigurations of the AWS Secret Manager integration should be clearer and better help identify the issue
- Fix trace uploads through the UI when STORAGE_USE_PUT is set to
23.12.0 - 2023-12-12↑
What’s new↑
- API & Backend
- Improve the performance of key and certificate matching during analysis. This should be especially visible when multiple analyses run in parallel.
- [GraphQL]:
- Added the
JiraIntegrationmodel toOrganization.integrations - Added several mutations to manage the updated JIRA integration
- Requesting
Slot.latestReportis now faster to respond
- Added the
- [Tanium]:
- The Tanium integration now generates better logging with more context
Bug fixes↑
- API & Backend
- Fixed trace uploads for users with the STORAGE_USE_PUT option set to
trueand the object storage server behind the same reverse proxy as the AQtive Guard server - Fixed a bug preventing reports of Network Captures to be deleted
- Fixed trace uploads for users with the STORAGE_USE_PUT option set to
23.11.2 - 2023-11-30↑
What’s new↑
- API & Backend
- [GraphQL]:
- Adding ability to query for key roles from operations field within GraphQL
- [GraphQL]:
Bug fixes↑
- API & Backend
- [GraphQL]:
- Requesting on GraphQL node without an inline fragment no longer raises an exception
- Requesting on GraphQL node with a different inline fragment than the one in ID no longer raises an exception
- Fix handling of special characters in passwords in the database URL
- [GraphQL]:
23.11.1 - 2023-11-22↑
What’s new↑
- API & Backend
- [GraphQL]:
- New type in the API:
RuleObjectType - New API field: `Rule.mainObjectTypes
- New type in the API:
- [GraphQL]:
Bug fixes↑
- API & Backend
- Logs for incoming requests are now correctly JSON formatted.
app.models.key.py::Key.informationmethod is now much more efficient. This should positively affect:- load-time of
Reportview - load-time of
Organizationdashboard view - GQL queries requesting
informationfield onKeyandOrganizationKeytypes
- load-time of
23.11.0 - 2023-11-15↑
What’s new↑
-
UI
- Improved readability of issue severity in the Project Dashboard and Report Issues views
- Updated the project dashboard inventory display to match Report and Organization inventory
- Introduced saved filters to organization dashboard
- Added saved filters to the URL so that when revisiting the page with the same UI, filters will be pre populated
- Turned filters on for the following pages:
- Organization certificates
- Organization keys
- Organization projects
- Project reports
- Report certificates
- Report handshakes
- Report keys
- API & Backend
- [GraphQL]:
- GraphQL query optimizations
- For instances of key-based rules, only the relevant key will be showed
- Added structured logs for all application logs
- [GraphQL]:
23.09.10 - 2023-11-08↑
What’s new↑
- API & Backend
- Add support for the AWS Secret Manager
- For instances of certificate-based rules, only show the relevant certificate.
- OpenID Connect: Allow the claim specified by OIDC_ROLE_CLAIM_NAME to point to a list of groups (not just one group).
Bug fixes↑
- API & Backend
- Improve validation of GraphQL IDs, for better error messages.
23.09.9 - 2023-10-20↑
What’s new↑
- UI
- Added saved filters to the organization dashboard
- **API & Backend
- GraphQL API
- Breaking changes:
- Field
Trace.size: Change type fromInttoBigInt.
- Field
- Breaking changes:
- GraphQL API
Bug fixes↑
-
UI
- Fixed a11y issues:
- organization dashboard responsiveness
- contrast colors on org dashboard graphs
- tooltips are “hoverable” for the accessibility
- checkbox groups are fixed with a11y changes
- Fixed a11y issues:
- API & Backend
- Fix for the user to be able to upload trace size larger than 2 GB
- Fixed an issue with hsm fuzzer seen when trying to generate a report after a successful upload
- Enable the default settings to log everything in the console
- Ability to vertically scale RQ_WORKERS in on-prem installation using below keys in the config file
- RQ_NUM_WORKERS customizes the number of calls to flask rq worker
- RQ_NUM_WORKERS_ANALYSIS customizes the number of calls to flask rq worker analysis
- The default value is set to 1. It should have no impact on users if not set.
23.09.7 - 2023-10-11↑
What’s new↑
- UI
- AQtive Guard jira integration enables users to submit tickets to Jira individually or in bulk. This integration is performed in the AQtive Guard Web Interface. You can configure Jira integration in two ways:
- Jira issue export: Export one or more instances to automatically create issues in Jira.
- Jira form integration: Launch an editable form to submit an individual instance as a Jira issue.
- AQtive Guard jira integration enables users to submit tickets to Jira individually or in bulk. This integration is performed in the AQtive Guard Web Interface. You can configure Jira integration in two ways:
- API & Backend
- GraphQL API
- Breaking changes
- Input field
CreateTraceInput.size: Change type fromInttoBigInt.
- Input field
- Breaking changes
- GraphQL API
Refer to the Jira integration for more details.
Bug fixes↑
-
UI
- The priority fix is now linked to the project dashboards
- API & Backend
- Fixed the issue where uploading a trace via the CreateTrace mutation failed when the trace size is more than 2GBs
- Fixed logging streams to have JSON-encoded audit logs show up in the regular logs if no specific LOG_FILE_AUDIT has been specified
- Add support for handling old host scanner traces
23.09.6 - 2023-10-03↑
What’s new↑
-
General
- New
cs debugcommand to diagnose issues for on-prem setups.
- New
- API & Backend
- OpenID connect: new configuration variable to list scopes to use (see
OIDC_EXTRA_SCOPES) - OpenID connect: refuse authentication if the final list of roles for a user is empty
- OpenID connect: new configuration variable to list scopes to use (see
Bug fixes↑
- API & Backend
- Improve loading times of non-optimized reports
23.09.5 - 2023-09-29↑
What’s new↑
- API & Backend
- Support a new way to verify S3 connectivity and rights by uploading/downloading a small amount of data. See the
STORAGE_EXTENDED_HEALTH_CHECKconfiguration variable for more information.
- Support a new way to verify S3 connectivity and rights by uploading/downloading a small amount of data. See the
23.09.4 - 2023-09-28↑
What’s new↑
- UI
- Updated Pages:
- Report Issues Tab
- Three column layout allows seeing more information at the same time and navigating through instances faster.
- Star and Dismiss for instances have been deprecated. Ability to export already starred / dismissed instances in the Exports tab remains.
- Added ability to “filter” issues and instances by severity
- Report Exports
- Inventory & issue overview has a new UI
- Report Issues Tab
- New Features:
- Network Analyzer Handshakes & Ciphersuites Tabs
- Network Analyzer reports now contain a Handshakes & Ciphersuite tab
- Ciphersuite table:
- Contains all ciphersuites that were selected and negotiated with
- Includes ability to filter by “selected” and “IETF recommended”
- Clicking on a ciphersuite navigates to the handshakes table filtered by that ciphersuite
- Handshakes table:
- Contains all the handshakes found
- Dashboard Exports
- PDF & CSV formats available
- Aggregated inventory and aggregated issues
- Jira form integration
- Ability to set up an issue collector for jira company-managed projects
- Network Analyzer Handshakes & Ciphersuites Tabs
- Updated Pages:
All new and updated pages are WCAG 2.1 AA and ADA compliant.
- API & Backend
- Revamped logging in web-findings and added audit logs including:
- option to log to a file instead of stdout
- option to log to a rotating file, the output file will be renamed to .<%Y-%m-%d_%H-%M-%S> daily
- option to log audit logs to a different file
- option to set audit log level separately from general log level
- an API to generate structured audit logs
- Updates to Tanium Integration
- Rate limiters for Tanium, configurable limits for the request rate to Tanium, to avoid system overload
- Tanium InfoSensor - Checks for new trace presence on the endpoint
- Tanium MonitorSensor - The sensor will provide information on any running host scanner process or the latest run, including status, runtime, memory, etc.
- Ability to configure Tanium settings per project instead of just organization level
- Automatic Report Generation
- Authentication & Authorization
- Support for tag based authorization
- Assigning roles based on OpenID Connect token claim
- Revamped logging in web-findings and added audit logs including:
23.09.3 - 2023-09-19↑
Bug fixes↑
- API & Backend
- Implemented printable layouts for report summary and org dashboard
- Accessibility fixes for report inventory and report export pages
23.09.2 - 2023-09-19↑
What’s new↑
-
UI
- Upgraded the following pages, including more powerful filtering capabilities.
- Organization Keys tab
- Organization Key Details page
- Organization Certificates tab
- Organization Certificate Detail page
- Upgraded the following pages, including more powerful filtering capabilities.
- API & Backend
- Improve performance of GraphQL queries which only do counting (i.e. with the
totalCountfield). - GraphQL API:
- Breaking changes:
- Field:
ReportDone.handshakes.- New parameter: filters:
HandshakesFilter. - New parameter: sorters:
[HandshakesSorter].
- New parameter: filters:
- Field:
- New field:
Rule.filterStatus.
- Breaking changes:
- Improve performance of GraphQL queries which only do counting (i.e. with the
Bug fixes↑
-
UI
- Accessibility fixes (color contrast, font & labeling adjustments), throughout a variety of pages including organization dashboard and report pages.
- API & Backend
- Fix a token verification failure in OpenID Connect integration. This would prevent users from logging in with some identity providers with an “at_hash” error.
- Improve the analysis of host scans so that a keystore location counts as one location for a given key even if that key appears several times in that keystore.
23.09.1 - 2023-09-07↑
What’s new↑
- UI
- The new UI is now available in the on-premises packages but disabled by default. Contact us if you want to try it out.
Bug fixes↑
- API & Backend
- Fix a token verification failure in OpenID Connect integration. This would prevent users from logging in with some identity providers.
23.09.0 - 2023-09-01↑
What’s new↑
-
General
- Product documentation has been restructured and describes the new UI.
-
UI
- Tanium integration: Computer Group setting is now set at the project level (formerly at the organization level).
- API & Backend
- Improve host scan instance deduplication.
- In the legacy UI, it adds a “Locations” box to show the path of keys related to an instance.
- Improve host scan instance deduplication.
Bug fixes↑
- API & Backend
- Both trace and potentially autocreated reports are marked as failed if there is a mismatch between trace/slot types.
23.08.2 - 2023-08-28↑
What’s new↑
-
UI
- When uploading a trace in an existing slot, the app lets the user choose the name of the trace/report.
- Inventory summary will show respective bars in the chart on printable export of report page.
- API & Backend
- GraphQL API
- Breaking changes:
Location.fileType: changed type fromStringtoFiletype.- New input fields:
CreateTraceInput.fileName: String. - New enum values:
InstancesFilterFields.number. - Input field
CreateTraceInput.name: changed type fromString!toString. - New fields:
Certificate.extensions,Certificate.signature,Certificate.version,Operation.tlsHandshake,OrganizationCertificate.extensions,OrganizationCertificate.signature,Rule.instances,Rule.severity. - New types:
Filetype,CertificateExtensionData.
- Breaking changes:
- GraphQL API
Bug fixes↑
- API & Backend
- Improve compatibility with OpenID Connect identity providers. Previously, login via OpenID Connect failed when the identity provider advertised support for multiple JWT signing algorithms.
- Fix that will allow to query handshake object from TLS handshake operations.
23.08.1 - 2023-08-24↑
What’s new↑
- API & Backend
- GraphQL API:
- New field:
ReportDone.rules. - New types:
RuleConnection,RuleEdge,RulesFilter,RulesFilterFields.
- New field:
- GraphQL API:
Bug fixes↑
- UI
- Fix an issue that prevented the report optimization status from being displayed after changes to the project exceptions.
23.08.0 - 2023-08-15↑
What’s new↑
-
UI
- Organization dashboard
- New functionality available:
- Ability to slice and filter the dashboard by tags, projects and profiles
- Aggregation of the instance count and percentages overall and across different analysis types
- Instead of the top 5 priority issues, you can now see a more extensive list
- Things that have changed:
- “Organization issues summary” information has been moved to the Projects tab, where you can see a breakdown of the issue count for each project.
- New functionality available:
- Projects page
- New functionality available:
- Projects can now be uncollapsed to show top priority issues for that project
- Top priority issues can be uncollapsed also to show the list of reports affected & breakdown of instances per report
- Horizontal bar per project with the number of high, medium, low and no warning issues
- Powerful filtering capabilities for: Name, Tags, Profiles, Last updated
- Things that have changed:
- To view and edit project information or assign testers, use the three dot menu on the right of each project.
- New functionality available:
- Slots, reports and traces pages
- New functionality available:
- Reports table contains the active / latest report for each slot
- Table contains information on the status of the report (e.g. failed, done etc.)
- Ability to filter by slot name and type
- In an upcoming release additional filters and sorters will be added
- Things that have changed:
- From the UI, cannot manually run a report from a trace, from the UI, reports will be analyzed automatically when uploading a trace using the profile defined for the project. Reports will be named after the trace name.
- From the UI, cannot run a report using a profile other than the default for the project in which it belongs.
- Must use the API if you wish to run a report using a different profile than the project default or run another report with an already uploaded trace.
- To see past reports in a slot, you must go into the latest report (accessible from the Project reports tab) and use the “Version” selector to select an archived report.
- The former “Slots” table has been replaced by the new “Reports” in which we show the latest (current) report from each slot.
- In order to change information about the slot or add tags use the three dot action menu on the right.
- New functionality available:
- The product version number is now visible in the user menu (top right corner).
- Organization dashboard
- API & Backend
- GraphQL API:
- New argument
sorters: [SlotsSorters]inProject.slots. - New enum values in
SlotsFilterFields:lastReportCreatedAt,lastReportState,lastReportTraceName. - New types:
SlotsSorter,SlotsSorterFieldsandState. - New fields:
Key.pkcs11Attributes,Key.source,Location.hostname,algorithmSummary,Operation.operationContext,Operation.operationType,Operation.report,Query.version,Report.project,Slot.distinctCallSites,Slot.lastReport,Slot.lastReportCreatedAt,Slot.lastReportState,Slot.lastReportTraceName,Slot.latestReport,Slot.reportCount.
- New argument
- GraphQL API:
Bug fixes↑
- API & Backend
- Fix inventory and stats on projects with multiple slots but only one trace type.
- Fixed pagination for
Organization.projects.
23.07.2 - 2023-07-26↑
What’s new↑
- API & Backend
- GraphQL API:
- Added GraphQL filters for report key and org key.
- GraphQL API:
Bug fixes↑
- API & Backend
- Fix so that network traces can be analyzed directly using the createTrace query
- Fix to retrieve operations data of an instance using the API
- Addition of filters on Instance nodes in GraphQL
23.07.1 - 2023-07-19↑
What’s new↑
- API & Backend
- Certificate filters are now available for network reports. This only applies to the legacy UI (the new UI already has filters for all certificates).
- Redis is no longer an external dependency of the AQtive Guard Analyzer
Platform all-in-one package: it’s built in and runs under the name
cryptosense-analyzer-redisin system. The distributed installation of AQtive Guard is unchanged.- Impact & user action required: Redis should be uninstalled on existing machines, preferably before the upgrade of the all-in-one package.
- GraphQL API:
- Breaking changes:
- Field
Operation.typechanged type fromOperationType!toString!. - Type
OperationTypewas removed. - Field
Rule.accesschanged type fromString!toString. - Field
Rule.consequenceschanged type fromString!toString. - Field
Rule.expertisechanged type fromString!toString. - Field
Rule.explanationchanged type fromString!toString. - Field
Rule.kbLinkchanged type fromString!toString. - Field
Rule.resourceschanged type fromString!toString. - Field
Rule.shortExplanationchanged type fromString!toString.
- Field
- New types:
CreateProjectExceptionInput,CreateProjectExceptionPayload,GeneralRemediation,JiraExportInstanceInput,JiraExportInstancePayload,JiraIntegration,OperationCategory,ProjectException,ProjectExceptionType,Remediation. - New fields in
Call,Instance,Operation. - New mutations:
createProjectException,jiraExportInstance.
- Breaking changes:
Bug fixes↑
- API & Backend
- Remove spurious log messages (containing the string
Record.t.key) during the analysis of PKCS#12 files. - Improve robustness of the installation of the on-premises AQtive Guard
packages by deprecating the use of the file
/etc/cryptosense-analyzer/package-variation. No action needed: it will be removed automatically when upgrading.
- Remove spurious log messages (containing the string
23.07.0 - 2023-07-13↑
What’s new↑
- API & Backend
- The on-premises RPM packages no longer depend on postgresql-libs but on libssl.so directly, which simplifies their installation
- GraphQL API:
- New types:
Overview,OverviewItem,OverviewSecure,OverviewSummary,OverviewWithMeta,ProfilesFilter,ProfilesFilterFields,InstanceStat. - New fields in
Organization,ReportVulnerability,Vulnerability. - New parameters:
filters: ProfilesFilteradded toOrganization.profiles. - New enum values in
ProjectsFilterFields:defaultProfile,lastUpdated,tags.
- New types:
Bug fixes↑
- API & Backend
- Fix network analysis in the on-premises package for Debian 10 and Ubuntu 18.04
- Fix the AQtive Guard on-premises packages to be installable again on Ubuntu 18.04
23.06.4 - 2023-07-11↑
What’s new↑
- API & Backend
- Support for Integrated Network Analyzer. Features include:
- Offline Analysis of PCAP files.
- PCAP files can be uploaded via API or directly via UI.
- Integrated Network Analyzer extracts below attributes from PCAP files. Below
attributes are available via GraphQL API
- Source IP
- Target IP
- Source Port
- Target Port
- Symmetric Encryption
- Selected Cipher Suite
- Client supported cipher suites (same attributes as selected cipher suite)
- Recommended ciphersuite as per IETF
- TLS version
- Certificate information (TLS 1.2 and lower). This will also be available via UI
- Key information
- RFC Reference
- Client timestamp
- Server timestamp
- Server name
- Captures incomplete handshakes
- Ability to apply rules to detect vulnerabilities for Certs and Keys.
- Ability to correlate Network scan certificates and keys across host and application reports.
- Crypto object inventory detected in PCAP traces
- Report summarization of vulnerabilities and issues based on rules applied on network trace crypto inventory
- Relationship between network trace keys and certificates
- Ability to extract keys and certificate specific fields via GraphQL API
- Support for Integrated Network Analyzer. Features include:
23.06.3 - 2023-06-20↑
Bug fixes↑
- API & Backend
- Fix GraphQL mutation
CreateTraceto create the trace with appropriate properties in the database when an existingdefaultSlotNameis chosen. Before this fix, the trace would be created but subsequent analysis of that trace would be refused by the server (with the error message: “This trace is still being processed”).
- Fix GraphQL mutation
23.06.2 - 2023-06-16↑
What’s new↑
- API & Backend
- PKCS#11 fuzzing report changes:
- In all reports, the “Vulnerabilities”/”Non-compliance” tab is now labeled “Issues” (legacy UI).
- Analyzing a PKCS#11 fuzzing trace results in only one generated report (instead of two). Existing PKCS#11 fuzzing reports are unchanged but they won’t be taken into account correctly in dashboards until they are regenerated after the upgrade.
- PKCS#11 “vulnerability” rule numbers are shifted by 200 (new = old + 200) to avoid colliding with the numbers of “compliance” rules.
- Improved the GraphQL field
Certificate.locationsto only return relevant locations. Before this version, it could return locations of the certificate’s public key or that of another certificate using the same key. - Remove field:
CreateTracePayload.reports: [Report]. - Add field
CreateTracePayload.report: Report.
- PKCS#11 fuzzing report changes:
Bug fixes↑
- API & Backend
- Fix a server error when
CreateTraceInput.generateReportistrueand the chosen trace name already exists. The server now replies correctly with an error message in such a case. - Fix an issue where the GraphQL field
Certificate.operationswould always return an empty list.
- Fix a server error when
23.06.1 - 2023-06-13↑
What’s new↑
- UI - Creating a new project supports a maximum of 100 reports per slot.
Bug fixes↑
- API & Backend
- There were some instances when the “stale private key rule” did not have any key linked to them. This fix added keys from keystore private key entries to objects and instances. As a side-effect you will see a “short encrypted private key in keystore” instance.
23.06.0 - 2023-06-01↑
What’s new↑
- UI: In this release, we’ve performed a significant overhaul of the dashboards,
issues, and inventory pages to provide a better and more intuitive user experience.
These changes lay the foundation for future enhancements, which will include dashboard
view customization and aggregate count creation. The changes below are already in our
SaaS product and for on-premises deployments you will be notified when these changes are
available.
- Organization Dashboard
- The dashboard is now organized by projects, displaying aggregate numbers for issues per project.
- Projects can be uncollapsed for more detailed insights, showing specific issues, the slots in which they occurred and the instance count.
- As we make a transition to the new UI, users will temporarily not be able to view Issue count + inventory summary at the organization level.
- Project Dashboard
- The Project Dashboard consists of two main components: Issues and Inventory.
- The ‘Issues’ section mirrors the structure of the Organization Dashboard, offering high level to detailed granularity, up to the instance level.
- The ‘Inventory’ section has been updated with a series of pie charts for a more comprehensive view.
- Report Inventory + Issues
- Inventory data is now presented via a series of pie charts.
- The “Crypto operation security” table has been deprecated, this information can be found in the “Issues” tab. The “Call sites limiting” has also been deprecated.
- The report metadata block allows users to change the report version, enabling quick navigation to different reports.
- We’ve released a new feature that allows you to give feedback quicker through the app. This “Report a bug” feature is located in the header.
- Organization Dashboard
- API & Backend
- Add ability to schedule report generation during trace upload with a new input field
CreateTraceInput.generateReport. - Bump version of PostgreSQL server in all-in-one on-premises deployments from 12.9 to
12.15. This is meant to increase its robustness and reduce the likelihood of data
corruption in those non-production deployments.
- No action required from the user and no migration necessary.
- Added a count of the number of vulnerability detection rules that were marked “disabled” in the chosen profile to the statistical summary of a report.”
- GraphQL API changes
- Modify field:
CreateProjectInput.profileIdis now required. - Add field:
CreateTraceInput.generateReport. - Add field:
CreateTracePayload.reports. - Add enum value:
DisplaySeverity.DISABLED. - Add fields:
Project.vulnerabilitiesandReport.vulnerabilities.
- Modify field:
- Add ability to schedule report generation during trace upload with a new input field
Bug fixes↑
- API & Backend
- Fix vulnerability statistics for projects and reports to not count disabled rules. This resolves a potential overestimation of the number of issues in each report or project.
23.05.3 - 2023-05-25↑
- Improve links between host scan instances and certificates to only link relevant
certificates (in the API this is materialized in the field
Instance.certificates).- This requires new reports to be generated for the links to work properly.
- GraphQL API:
- Modify the field
Instance.certificatesto show only relevant certificates. Before this change, it would also list irrelevant certificates with the same public key as the relevant certificate.
- Modify the field
23.05.2 - 2023-05-25↑
- Add ability to change project testers and max item count via the GraphQL API.
- Add support for the use of a custom SQL database schema on premises in a highly
available deployment (instead of the default
publicschema). This is controlled by a new configuration parameter:DATABASE_SCHEMA. - Remove support for database URLs with the
postgres://prefix. The only supported URL scheme is nowpostgresql://.- No action is needed for the user: configuration will be updated automatically when the new AQtive Guard package is installed.
- GraphQL API
- Add fields:
CreateProjectInput.maxItemCount,Project.maxItemCountandUpdateProjectInput.maxItemCount. - Add fields:
Organization.testers,Project.testersandUpdateProjectInput.testers.
- Add fields:
23.05.1 - 2023-05-16↑
- Improve links between host scan instances and keys to only link relevant keys (in the
API this is materialized in the field
Instance.keys).- This requires new reports to be generated for the links to work properly.
- Fix parsing of host scan traces with tags in the header (generated with the
--tagsCLI parameter of the host scanner). - Fix the profile creation form to show correct applicability of rules to the analysis of OpenSSL traces.
- GraphQL API:
- Modify the field
Instance.keysto show only relevant keys. Before this change, it would also list irrelevant keys at the same filesystem location as the relevant keys. - Add types
IntegrationandTaniumIntegrationand add fieldOrganization.integrations.
- Modify the field
23.05.0 - 2023-05-02↑
- Fix bug where users would sometimes end in an infinite redirect loop at login.
- GraphQL API:
- Add
Locationnode with connections toKey,CertificateandInstance. - Add
ReportVulnerability,OrganizationCertificatenodes. - Add
methodfield to the response of thegenerateTraceUploadPostmutation. - Add
deleteSlotmutation.
- Add
23.04.2 - 2023-04-18↑
- GraphQL API:
- Add
OrganizationKeyand related types. - Add fields:
Organization.keys,Key.organizationKey. - Rename field
Key.keyMetadatatoKey.metadata. - Rename field
Key.keyTypetoKey.type. - Rename field
Key.keyCategorytoKey.category.
- Add
23.04.1 - 2023-04-11↑
- Add support for tags in the AQtive Guard UI.
- GraphQL API:
- Add
HandshakeandTlsHandshakeobjects - Add sorters to
Organization.profiles - Expand project
VulnerabilitySlotwith latest report id
- Add
23.04.0 - 2023-04-06↑
- API:
- Fix crash when fetching instances of a report without a profile
- Add sorters and filters to
Organization.projects - Update
updateSlotmutation with tags - Add fields:
Project.tagsVulnerability.slotsProject.vulnerabilitiesReport.firstAnalysis,Report.lastAnalysisandReport.distinctCallSites
23.03.5 - 2023-03-27↑
- Fix deletion of host scan reports. A failure caused reports to stay in the database.
- Previous failures will be handled after upgrading and deleting one report.
- GraphQL API:
- Add fields:
Mutation.deleteProjectProject.vulnerabilityStatistics: Rule counts for each severity, at the project level.Project.lastUpdatedOrganization.allowedTraceTypes: Types of traces that users can analyze in this organization.Trace.size
- Add fields:
23.03.4 - 2023-03-22↑
- GraphQL API:
- Rename type
ApitoTraceType. - Rename fields
apitotraceTypethroughout the API (Slot,Trace,Report, etc).
- Rename type
23.03.3 - 2023-03-21↑
- Improve the logging of failed Jira operations.
- GraphQL API:
- Remove duplicate
apitype in favor of the existingAPItype. - Rename
valuestosubFiltersinSlotsFilter,ReportsFilteretc. - Add filtering of slots based on their tags with a new
CONTAINSoperator. - Add fields:
Mutation.updateProject: change the attributes of a project.ReportDone.inventory: statistics about a report.Report.apiTrace.api
- Remove duplicate
23.03.2 - 2023-03-10↑
- GraphQL API:
- Link host scan instances to keys and certificates via locations. The
Key.instances,Instance.keysandCertificate.instancesfields will now return more results by linking results through the location of the node.
- Link host scan instances to keys and certificates via locations. The
23.03.1 - 2023-03-10↑
- Maintenance release
23.03.0 - 2023-03-07↑
- GraphQL API:
- Add field:
Key.report. - Add field:
Certificate.report. - Add field:
Operation.keys. - Add field:
Project.organization. - Add
defaultSlotNametoCreateTraceInput.
- Add field:
- Check for slot/trace API compatibility:
- Display error if different API for slot and trace.
- Display error if organization does not have rights on API.
- Introduce a view for traces that have no slot. Happens for pending or failed traces uploaded by the user without specifying a destination slot.
23.02.4 - 2023-02-26↑
- GraphQL API:
- Add type:
SignatureAlgorithmand link it toCertificatenode. - Add nodes:
CallSiteandOperation. - Add fields:
Certificate.notBefore,Certificate.notAfterandCertificate.signatureAlgorithm. - Add fields:
Trace.reports,Trace.jvmName,Trace.jvmVendor,Trace.jvmArgumentsandTrace.javaClassPath. - Add field:
Report.url.
- Add type:
23.02.3 - 2023-02-23↑
- GraphQL API:
- Simplify filters and sorters enum names.
ProjectsFilterFilterFields(resp. Traces, Slots and Reports) is nowProjectsFilterFields.ProjectsSorterSorterFields(resp. Traces, Slots and Reports) is nowProjectsSorterFields.
- Make the AnalyzeInput.profileId parameter optional.
- Add fields:
Certificate.isCaandCertificate.isSelfSigned. - Add fields:
Report.profileandReport.trace. - Add field:
Project.description. - Add
descriptiontoCreateProjectInput.
- Simplify filters and sorters enum names.
- On-prem:
- Support AWS IAM Role-based authentication for S3.
- Projects can now have a default profile. This lets the user analyze a trace or scan without specifying a profile.
23.02.2 - 2023-02-14↑
- GraphQL API:
- Add types:
InventoryRecapLineData,InventoryRecapCategoryandInventoryRecapData. - Add fields:
Certificate.publicKeyandKey.certificates. - Fix
Key.idandCertificate.idfields: they were in the wrong format. - Fix
Key.lengthandKey.keyMetadatafields: queries with those fields would fail.
- Add types:
23.02.1 - 2023-02-09↑
- OpenSSL analysis: Fix an analysis error occurring when two certificates or more are inserted into the database.
- GraphQL API:
- Add field:
Organization.name.
- Add field:
23.02.0 - 2023-02-01↑
- Add support for Shrouded Keybag in PKCS#12 host scan analysis.
- GraphQL API
- Introduce generic filters:
Project.reportshas one new parameter:sorters.User.projectshas two new parameters:filtersandsorters.
- Add fields:
Trace.slot,Report.slot,Slot.projectandProject.slots. - Add an
updateSlotmutation to change the properties of a slot.
- Introduce generic filters:
- Fix a rendering error on the slot details page when the latest report isn’t linked to a trace.
- Fix a rendering error on the slot details page when the latest report is in the “failed” state.
- On the project details page, replace the obsolete “trace” and “report” links with a “slot” link.
23.01.4 - 2023-01-30↑
- Link instances to keys and certificates in the API
- Add
Ruletype to instances in the API. - Fix issue in the
createProjectmutation where users would not be linked to projects. - Add missing “Stored Key” operation filter to keys table.
23.01.3 - 2023-01-23↑
- Maintenance release
23.01.2 - 2023-01-18↑
- Improve compatibility of OpenID Connect integration.
- Fix report diff creation: Diffs were created without being assigned to a slot.
- Fix
User.projectsfield in the API when used with pagination arguments.
23.01.1 - 2023-01-10↑
- Fix handling of special characters in certificate search.
- Fix analysis of PEM files: If one PEM element couldn’t be analyzed, it would cause the whole file to be dropped.
23.01.0 - 2023-01-03↑
- Add analysis of PKCS#7 files found by the host scanner.
22.12.2 - 2022-12-19↑
- Fix the trace/report auto-deletion threshold to work with slots.
- Fix the computation of the “has private key” property for keys when reports have been deleted.
- Add new analysis pipeline for OpenSSL (libssl) traces.
- Add analysis of PuTTY private key (PPK) files found by the host scanner.
22.12.1 - 2022-12-05↑
- Add “View traces” and “View reports” buttons to the slots page.
22.12.0 - 2022-12-05↑
- Traces and Reports are now organized into Slots inside their project. Multiple traces of the same type can now be analyzed in parallel in the same project.
- Add support for the PPK format.
22.11.0 - 2022-11-28↑
- Added EC analysis to Evp
22.10.2 - 2022-10-28↑
- Added optional
resourceparameter to OpenID Connect authorize URL.
22.10.1 - 2022-10-24↑
- Improved performance of keys and certificates pages at the organization level.
- Fixed error when OpenID server is unavailable by falling back to classic login.
22.10.0 - 2022-10-07↑
- Add option to search projects by name through the API.
- Add option to use OpenID Connect and Ping Federate for the on-premise version.
22.09.1 - 2022-09-07↑
- Fix the deletion of projects.
22.09.0 - 2022-09-05↑
- Fix bugs appearing when uploading and analyzing a large number of traces in parallel.
- Traces and reports will now be timed out and marked as failed after 2 hours and 4 hours respectively.
- Make traces / reports names and descriptions editable in their summary box.
- OpenSSL (libcrypto) analysis now supports more cipher algorithms.
- Improve the overall quality of the filesystem analysis with a new implementation.
- Add the analysis of cleartext data in PKCS#12 keystores from filesystem scans.
- Optimize the computation and improve the appearance of keys and certificates tables.
22.07.5 - 2022-07-26↑
- Add support for SHA-2 and SHA-3 algorithms in OpenSSL libcrypto analysis.
22.07.4 - 2022-07-26↑
- Pending traces and reports will now be marked as failed after a while.
- Link report key to corresponding org key, report cert to its public key, report cert to corresponding org cert, org cert to its public key and org key to all corresponding org certs.
22.07.3 - 2022-07-26↑
- Avoids accumulation of files resulting from incomplete uploads (e.g. because of a client error) by automatically removing those files after a certain time.
- Add “Export” and “Compare” buttons to a report’s “Inventory” page.
- Add the current AQtive Guard version to the footer.
- Add a “Keys” column to the operations table in an instance details page, with links pointing to the related keys for each operation. This only applies to application tracing.
22.07.2 - 2022-07-12↑
- Maintenance release.
22.07.1 - 2022-07-12↑
- Fix analysis failures not being reported as such in the AQtive Guard Analyzer Platform. This could lead to some traces or report to get stuck in an “in progress” state.
- Improve visual appearance of report details so that it matches that of trace details more closely.
22.07.0 - 2022-07-04↑
- Fix an occasional analysis failure for PKCS#11 traces.
- Avoid log warnings when analyzing concatenated trace files.
22.06.1 - 2022-06-17↑
- Harden the CSP header to prevent the execution of inline JavaScript. This is an additional fix to defend against potential future XSS attacks.
- On the main dashboard in the “Organization Issue Summary” bar chart, merge bars for the same project.
- Add pagination to the organization certificates details page.
22.06.0 - 2022-06-13↑
- Harden the CSP header to restrict possible connections. This is an additional fix to defend against potential future XSS attacks.
- Update dependencies to secure versions. The security of AQtive Guard was not affected overall.
- Add pagination to the organization keys details page.
- Add a button to test the Venafi integration configuration.
- Add an option to define custom certificates for the Venafi integration.
- On the main dashboard in the “Overview”, replace the number of applications/filesystems/tokens and the number of traces by just the number of projects (relevant to each category: application/filesystem/PKCS#11 token).
22.05.8 - 2022-05-25↑
- Update dependencies to secure versions. The security of AQtive Guard was not affected overall.
- Fix stored XSS on the certificates details page. This vulnerability could be triggered through manipulated traces. No indication of attempted attacks were found, but if you have AQtive Guard on-premises, upgrading is highly recommended.
22.05.7 - 2022-05-24↑
- Update dependencies to secure versions. The security of AQtive Guard was not affected overall.
- Fix analysis of certain libssl traces.
- Fix the analysis of Fermat attack on RSA to mark safe RSA keys as “Passed”.
22.05.6 - 2022-05-19↑
- Fix
totalCountfield for some connections in the GraphQL API (for example:ReportConnectionin aProject). - Improve error message in the GraphQL API when the ID of a profile, project, trace or report can’t be found by the server.
22.05.5 - 2022-05-06↑
- Rules specific to the Host Scanner are no longer included in FIPS specific profiles.
- Improved appearance of the organization certificate details page.
- Fix analysis of certain certificate chains picked up by the host scanner.
22.05.4 - 2022-05-05↑
- Maintenance release.
22.05.3 - 2022-05-04↑
- Maintenance release.
22.05.2 - 2022-05-03↑
- Maintenance release.
22.05.1 - 2022-05-03↑
- Maintenance release.
22.05.0 - 2022-05-02↑
- Add rule for Java applications: Psychic signatures (CVE-2022-21449).
- Add rule for hosts and applications: Fermat attack on RSA (CVE-2022-26320).
- Sanitize Venafi instance URL: a trailing slash no longer causes invalid links to be generated by AQtive Guard.
- Add
createdAtdate field totraceandreporttypes in GraphQL API. - Remove
apifield fromprojecttype in GraphQL API. - Add
deleteReportmutation to GraphQL API. - Improve appearance of organization key details page.
- Improve parsing of PKCS#11 usage traces.
22.04.3 - 2022-04-15↑
- Improve performance of the organization keys page.
22.04.2 - 2022-04-14↑
- Improve loading time for report keys page.
22.04.1 - 2022-04-14↑
- New organization certificates tab.
- New page to display details of a key at the organization level.
- Fix broken link in trace upload tutorial
- Fix keys tab filter to stop hiding keys of unknown length
22.04.0 - 2022-04-04↑
- Existing projects are no longer tied to a specific type of trace and can now contain any type of trace allowed by the organization.
22.03.7 - 2022-03-31↑
- Fix a bug that would appear when the wrong files are uploaded to recent projects.
- Add a
keptByFilters: Booleanparameter toReportDone.instancesfield in the GraphQL API.
22.03.6 - 2022-03-18↑
- Add “Cryptosense 2022” profiles for everyone.
- Check if a profile can be deleted before asking the user for confirmation.
22.03.5 - 2022-03-16↑
- Add Jira integration:
- The link to a Jira instance can be configured in the “Integrations” tab.
- Users can then export individual findings as Jira issues.
- Findings can also be exported in batches.
- Add a Host Scanner download button for users authorized to analyze host scans.
- Improve performance of dashboards for key store statistics coming from newly generated host scanner reports. This doesn’t affect performance for existing reports.
- Improve report generation performance when the organization has a lot of keys.
- Add “Date Uploaded” and “Uploaded By” to traces in the project “Traces” tab.
- Fix rule and instance counts in report export printable view.
22.03.4 - 2022-03-09↑
- Update text shown only to users of the free demo account.
22.03.3 - 2022-03-09↑
- Maintenance release.
22.03.2 - 2002-03-08↑
- Add 5 new application analysis rules related to post-quantum readiness. Those rules are disabled by default.
- Add a new “Post Quantum Readiness” builtin profile using only the aforementioned rules
22.03.1 - 2022-03-04↑
- Fix a bug where the severity of certificate digest findings in host scan reports was not set to low for self-signed certificates inside keystores.
22.03.0 - 2022-03-02↑
- Fix potential database synchronization issues associated with the organization keys table and automated deletion of old reports.
- Fix overflow of a table in the report print view.
22.02.4 - 2022-02-18↑
- Add a
completedAt: Stringfield to theReporttype in the GraphQL API. - Add a
url: Stringfield to theInstancetype in the GraphQL API.
22.02.3 - 2022-02-16↑
- Fix CSV export of findings: the file was empty for some types of reports.
22.02.2 - 2022-02-15↑
- Add new application analysis rule: “Asymmetric key-transport key outside cryptoperiod”.
- Enforce the uniqueness of project names within each organization.
- In host scan reports, set severity of certificate digest findings to low if the certificate is self-signed.
22.02.1 - 2022-02-08↑
- Maintenance release.
22.02.0 - 2022-02-01↑
- Add organization keys tab. This shows all keys found in reports generated from now on. To see keys from old reports, you will need to run them again.
22.01.4 - 2022-01-31↑
- Add help tooltips for some certificate filters: “Self-signed” and “CA certificates”.
- Improve performance of the “Certificates” tabs in all analyzer reports.
22.01.3 - 2022-01-21↑
- Fix database migration script.
22.01.2 - 2022-01-21↑
- Add pagination information (page number and next/previous page links) to the bottom of paginated lists.
- Fix serialization and parsing of some key metadata.
22.01.1 - 2022-01-14↑
- Fix issue with the filters for self-signed and CA certificates that caused some certificates to be hidden.
- Add filters for key lengths to the keys and certificates tabs.
22.01.0 - 2022-01-10↑
- Hide the “has-private-key” attribute in the key detail page for symmetric keys.
21.12.2 - 2021-12-29↑
- Improve the performance of the “Keys” tab in host scanner reports, especially when the database contains a large number of file entries.
21.12.1 - 2021-12-20↑
- Add the following rules to Java analysis:
- Invalid certificate
- Certificate validity too long
- Extract certificates from
KeyStore.getCertificateChaincalls in Java. - Show organization name on dashboard.
21.12.0 - 2021-12-13↑
- Add filters for key file type in host scanner reports
- Add filters for self-signed and CA certificates for Java and host scanner reports.
- Operations are now ordered by last call
- Include Host Scanner rules into tracer profiles
- Display compatible API for rules on the profile page
- Improve performance of the keys tab in host scan reports.
- New projects are multi-type, they can handle multiple trace types at once and summarize them.
21.11.3 - 2021-11-26↑
- Fix parsing of X.509 certificate extensions, which caused wrong interpretations of whether some certificates are CA certificates or not.
21.11.2 - 2021-11-25↑
- On the certificate details page, show whether a certificate is self-signed or a CA certificate.
- Added certificate expiration and stale key warning limits to the profile.
21.11.1 - 2021-11-18↑
- Display file type in key information column for keys tab in host scan reports.
- Fix bug where all key files in a host scan were categorized as SSH keys. Key files are now categorized as SSH, PGP, PKCS#8, etc.
- Change location stats computation: previously it was counting instances; now it counts locations and the maximum severity per location.
21.11.0 - 2021-11-16↑
- First numbered version.