Network Analyzer↑
The AQtive Guard Network Analyzer is designed to analyze cryptographic activity within network traffic. By parsing network handshake-related information, it identifies cryptographic protocols, certificates, and keys used in data transmission, enabling insights into encryption methods across your network.
The AQtive Guard yanadump tool complements network analysis by enabling live traffic monitoring, providing continuous visibility into network activity.
It analyzes encrypted traffic within monitored connections, assessing the use of supported protocols and providing actionable insights without accessing exchanged data or relying on pre-captured PCAP files.
Download↑
To download yanadump:
- Log in to AQtive Guard as an administrator.
- Select Settings from the menu bar, then select Sensors.
- Select Download under the Network Analyzer tile.
When to use Yanadump↑
Tip
If you already have a PCAP file, or would like to create one for analysis, you can skip this section and refer to Getting started with PCAP upload.
Analyzing networks at the scale of gigabit Ethernet links presents challenges due to the high data volume. Since the data is too large to capture and save on disk, it needs to be analyzed as close to the network traffic as possible.
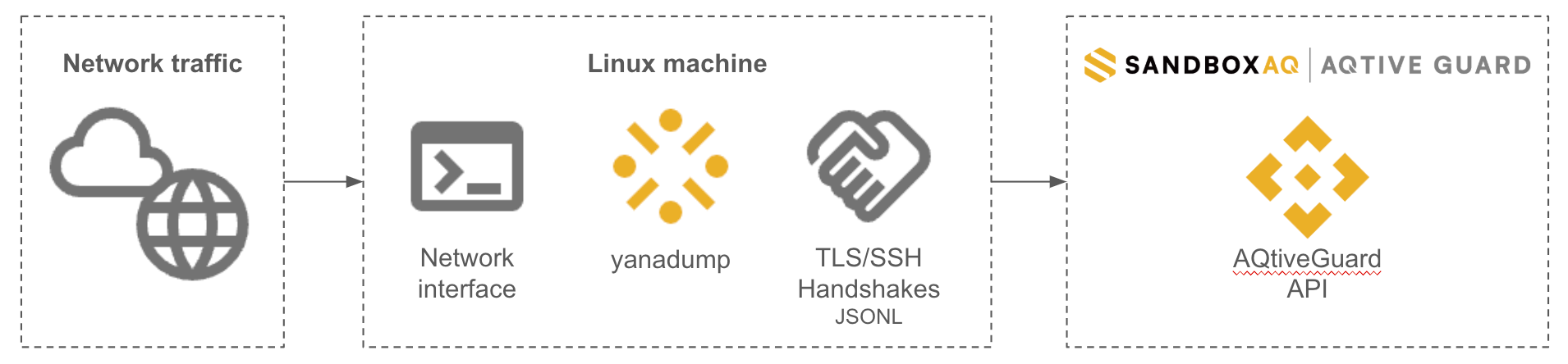
Yanadump is a high-efficiency network analyzer developed by SandboxAQ to capture and process cryptographic data on high-speed networks. It operates as a standalone, portable Linux binary optimized for environments where high network speeds and large data volumes make storing full packet captures (PCAPs) impractical.
Instead of saving complete PCAP files, yanadump processes traffic in real time and generates compact jsonl files containing only the relevant cryptographic details, as shown in the following diagram:
Key yanadump features include:
- Efficient Data Reduction: Reduces a 40GB PCAP to a 117MB
jsonlfile (0.3% of original size), further compressible to 17MB (0.04%). - Targeted Information: Extracts only handshake-related information, supporting efficient cryptographic analysis.
- Protocol Support: Supports Ethernet, 802.1Q (VLAN), GRE, IPv4, IPv6, and VXLAN, making it adaptable to various network configurations, including cloud environments.
- Scalability: Achieves traffic parsing speeds of approximately 1Gbps per CPU GHz, suitable for gigabit-scale networks.
For yanadump deployment details, refer to Getting started with live network traffic monitoring.