Report fundamentals↑
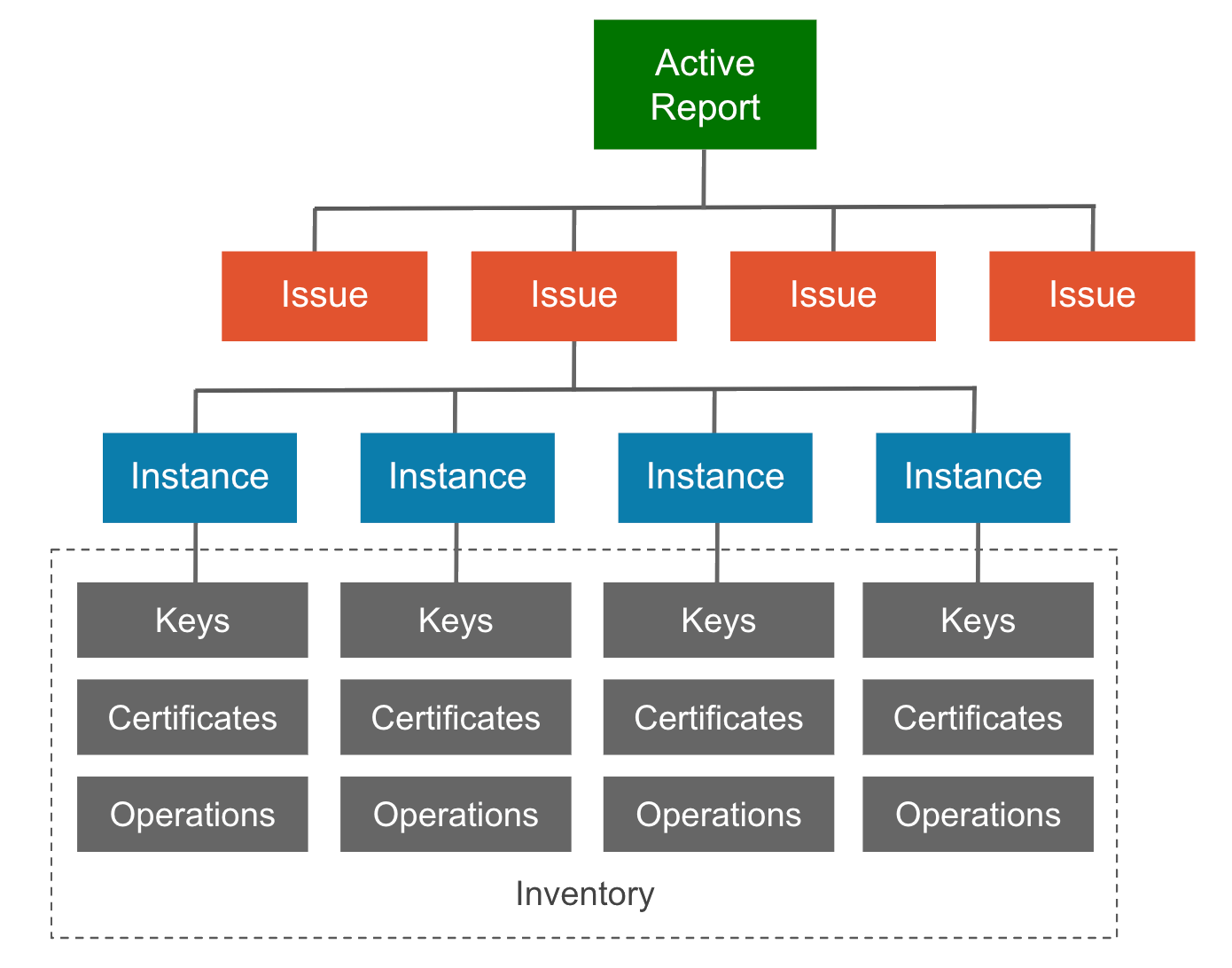
When you initiate an analysis, AQtive Guard uses rules established in the selected profile to evaluate the uploaded trace. The resulting report presents information in a logical hierarchy:
- Issue: reports the severity level or status of discovered cryptography that was evaluated against a given rule. A Priority issue indicates one or more instances failed to pass the evaluation.
- Instance: records the findings and details each time a rule is detected and evaluated, including applicable:
- Best practices and recommended remediation
- Operations
- Call sites
- Inventory: maps the cryptography associated with each instance, including keys, certificates, and operations.
Report walk-through↑
The following scenario walks you through the steps to find a report and view its Issues, Instances, and Inventory so you can investigate the cryptographic findings.
Project Overview↑
Start by locating the project where the analysis was run:
-
Select Projects from the menu bar to open the Projects table.
-
From the first column of the table, select the desired project name to open the project Overview.
This displays the Issues and Inventory Summary of cryptographic elements within the selected project.
Tip
You may need to scroll to see all the information.
Reports table↑
To continue your investigation, open a report for an individual analysis:
-
Select Reports to open the reports table.
This displays the active (most recent) reports and associated slots in the selected project.
-
Select the desired Report Name from the second column of the table to open the Issues tab for that report.
Issues tab↑
Interact with the information in the Issues tab to reveal details about an Issue, its rule, and its Instances:
- Select an issue in the left column to view all discovered Instances.
- Select Show Issue Details to access information about the rule.
- Select Instances to reveal additional details, such as Operations, if applicable.
Note
The information provided will vary based on the report type and findings.
Issues are grouped by their status at the time of the analysis. A Priority issue indicates one or more instances failed to pass the evaluation. See Issue fundamentals to learn more.
Summary tab↑
To access information about the cryptographic items identified during the analysis, select the Summary tab to review details:
- Inventory: a visual representation of the cryptography discovered in the analysis, including algorithms, keys, and key storage.
- Crypto Library Security: the cryptographic providers detected in the trace.
- Statistics: specific details related to security items reported, such as hash functions and signatures.
- Report Details lists metadata for the displayed report, including:
- Name of the report
- Version (date and time of the analysis)
- Size of the report
- Trace used for analysis
- Profile used for analysis
Tip
To view an earlier version of this report, select the Version dropdown.
Export tab↑
Select the Export tab to print or export report data for the selected analysis. Select from the following report options:
- Print - print selected data (default PDF)
- CSV - export selected data in CSV format
- JSON - export the full analysis in JSON format
- Jira - export one or more instances as Jira issues. This requires the Jira integration.
- ServiceNow - export one or more instances as ServiceNow incidents. This requires the ServiceNow integration.