Information hierarchy↑
A clear information hierarchy helps you navigate AQtive Guard. The Web Interface visually presents data, and selecting items in the Dashboard, tables, and reports offers detailed cryptographic information.
Organization↑
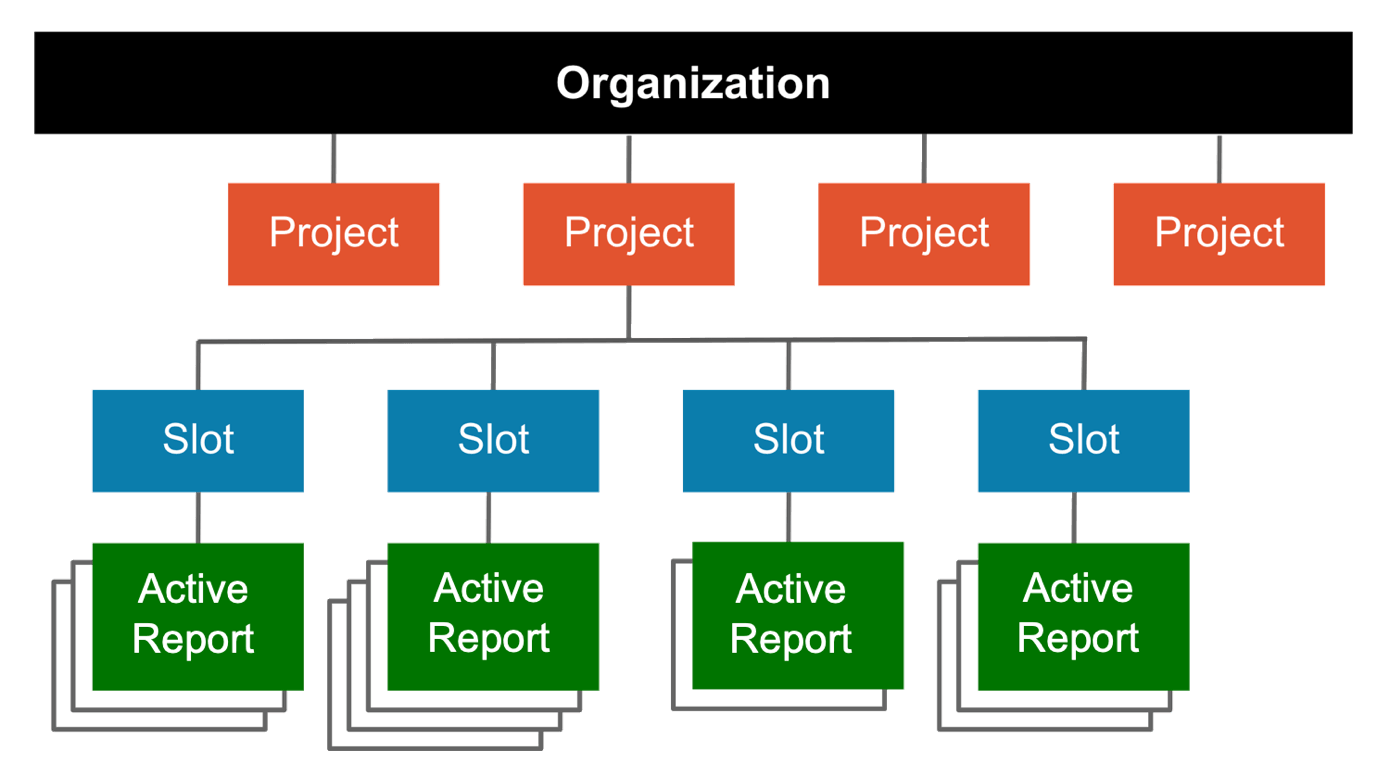
The highest information level of AQtive Guard is the Organization. You’ll find your organization name at the top of the Dashboard, which provides an aggregated view of your cryptography across all active projects.
The diagram that follows illustrates the Organization hierarchy:
Project↑
A Project provides a way to organize slots. An Organization can have multiple projects, and each user can be given access to one or more projects. When you set up a new project, you select a profile to control its analysis rules and thresholds.
Slot↑
A Slot contains an active report and an archive of previous versions. Each version is generated by uploading a trace to the slot. As the trace evolves, it should be uploaded to the same slot.
A project can have multiple slots. It’s recommended to associate each slot with a project asset, like a backend authentication service, network captures, or front-end code.
Refer to Slot fundamentals for more details.
Report↑
During analysis, AQtive Guard assesses the uploaded trace based on project profile rules and thresholds. The report displays an inventory of discovered cryptography, including key, certificate, handshake, and cipher suite details. Each rule analysis is recorded as an Instance within the corresponding Issue.
Refer to Report fundamentals for more details.
Report Hierarchy↑
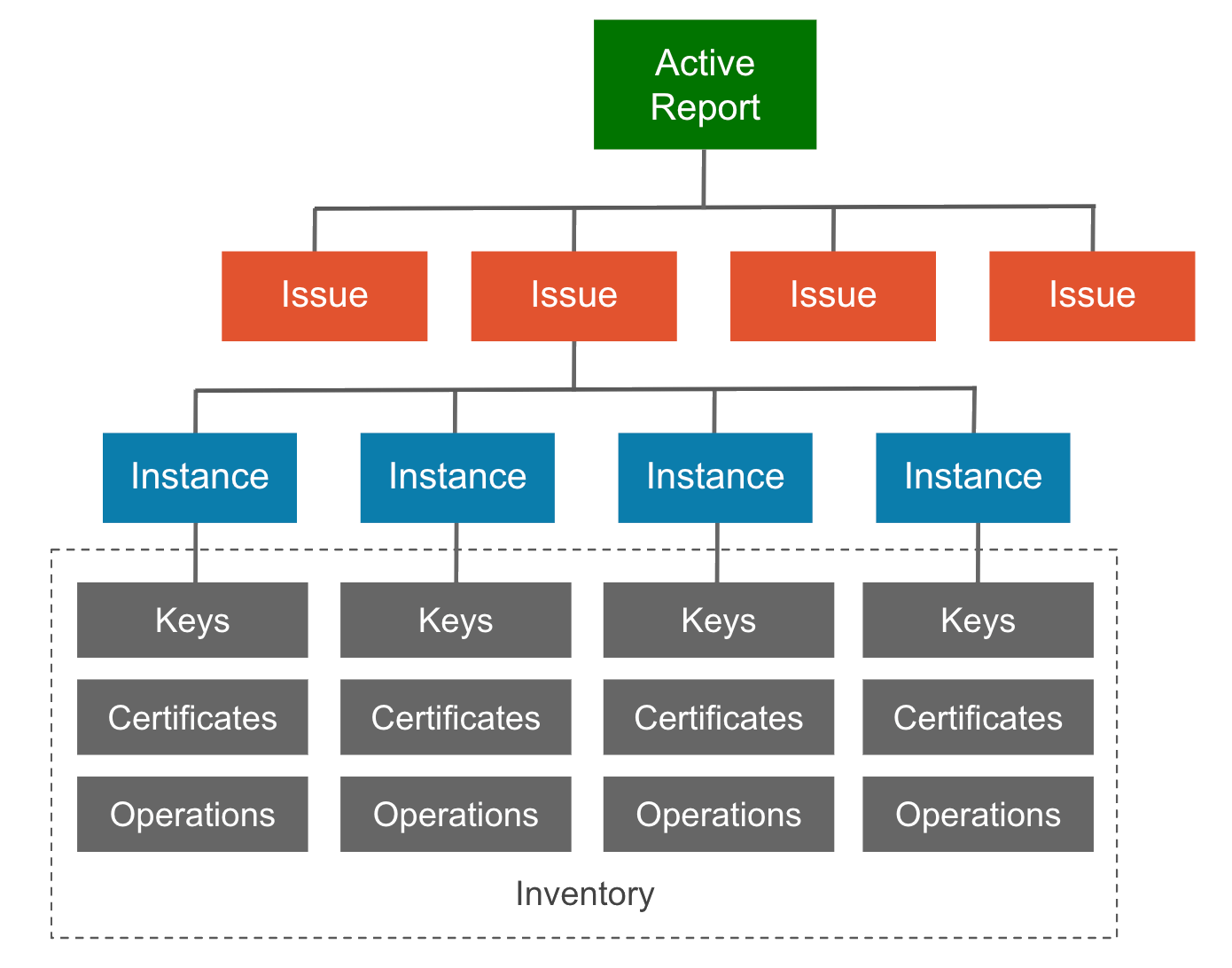
The logical information hierarchy extends through the Report, as shown in the following diagram.
Issue↑
An Issue reports the severity level or status of each instance of cryptography that was evaluated against a given rule. A Priority issue indicates one or more instances failed to pass the evaluation.
Instance↑
Instances record the findings and details each time a rule is detected and evaluated, including applicable:
- Best practices and recommended remediation
- Operations
- Call sites
Refer to Issue & Instance fundamentals for more details.
Inventory↑
Your cryptographic inventory maps the cryptography associated with each instance, including keys, certificates, and operations.